Application and API onboarding
Overview
API onboarding is a crucial step in managing and securing your API ecosystem. Using OpenAPI specifications, you can efficiently onboard applications while ensuring consistency, documentation, and security compliance. This section provides guidance on how to onboard applications and APIs using OpenAPI specs, making the process structured and repeatable.
What You'll Learn
- How to onboard an application using an OpenAPI spec
- Steps to ensure API specifications are properly defined
- Best practices for integrating API security during onboarding
Getting Started with API Onboarding
Understanding OpenAPI Specifications
An OpenAPI Specification (OAS) provides a standardized format to describe your API, enabling:
- Automated API documentation
- Consistent API definitions across teams
- Simplified integration with security and testing tools
Validate your OpenAPI spec using tools like Swagger Editor to catch errors before onboarding.
If your API already has an OpenAPI spec (.json or .yaml), you can use it for a streamlined onboarding process.
Access the API Onboarding Section
- Navigate to the API Management dashboard.
- Click "New Application" to begin onboarding.
Select the OpenAPI Specification Method
- Choose "Onboard using OpenAPI Spec" from the available options.
- Click on the "Next" button.

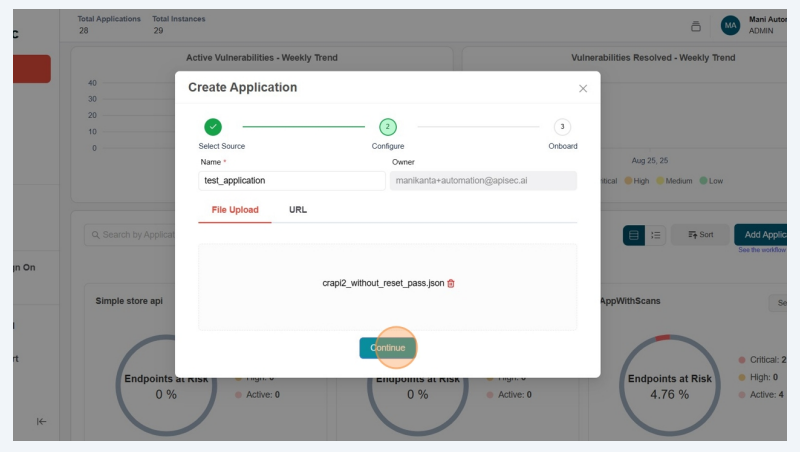
Enter Application Details
-
Provide an application name.
-
Click on "Browse Files" and Upload the API’s OpenAPI file
-
After uploadint the document, click on the "Continue" button.
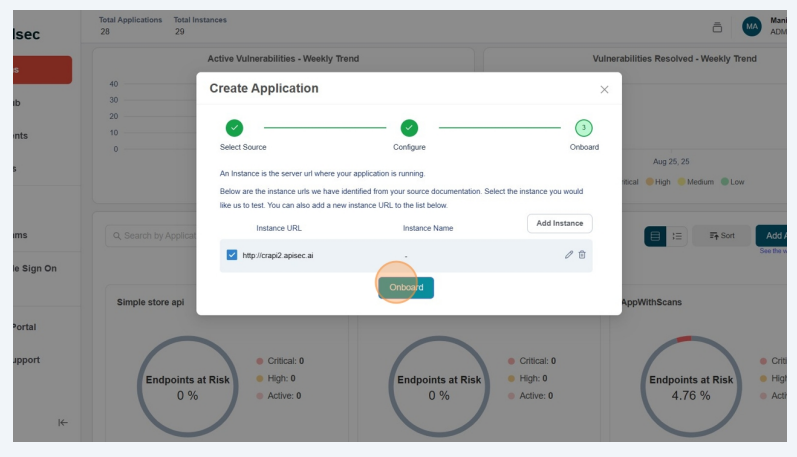
Review and Confirm
-
Validate that the Instance and click on "Onboard" button.
Complete the Onboarding Process
-
Finalize the onboarding and view your API in the dashboard.
Once your API is onboarded, you can:
- Test API security to identify vulnerabilities
- Enable monitoring to track API usage and performance
- Integrate with API gateways for traffic management and security enforcement
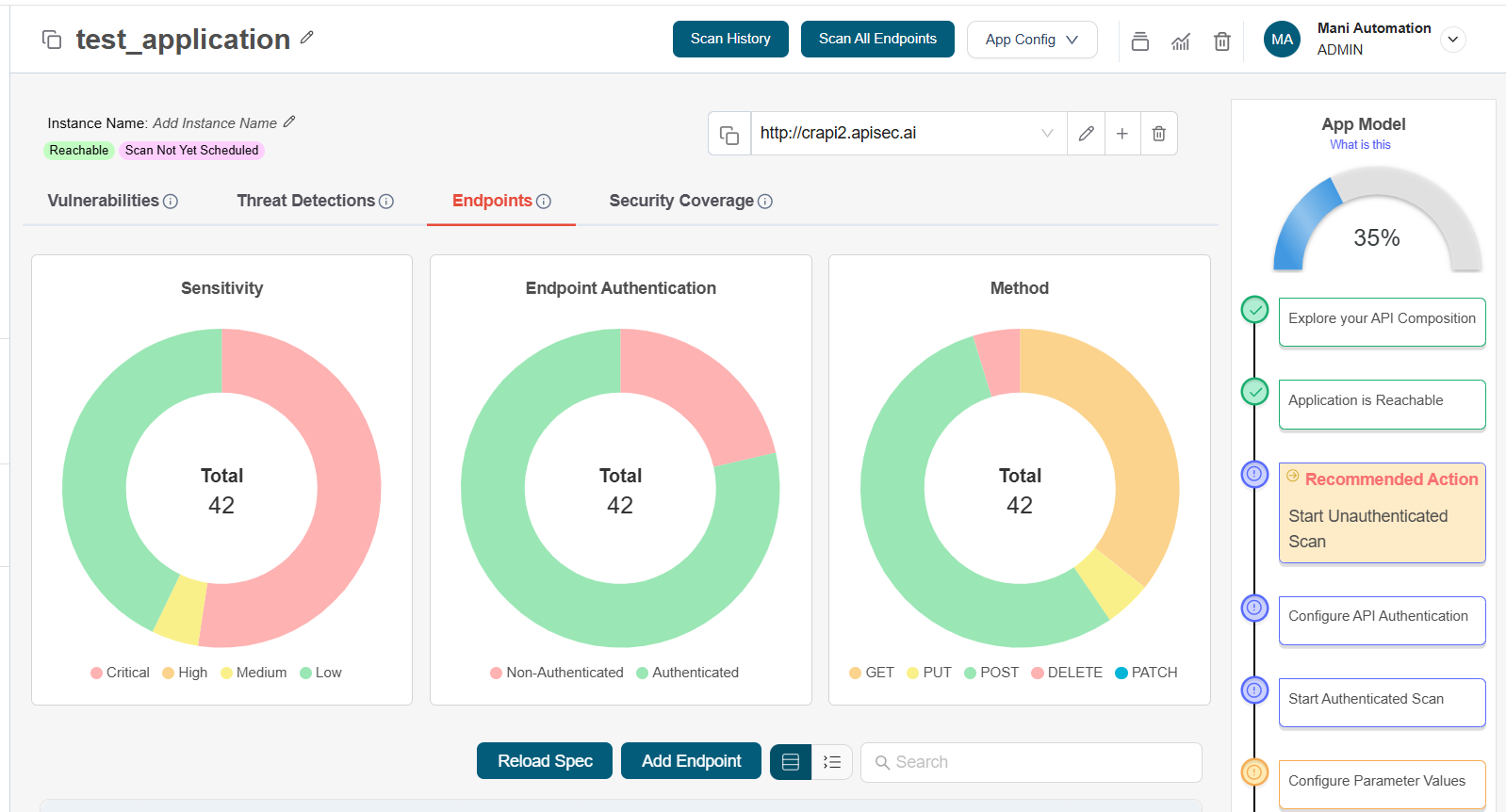
In application details page, you can find the application name, reachability status, scan status, and the Instance URL of your application"
Update Application Name
- Click the Pencil icon next to the application name to edit and update it.
Users with View permissions cannot update shared application name
Add/update instance name
- Click the Pencil icon next to Add instance name to edit and update it.
Users with View permissions cannot add/update instance name in shared application
Edit instance URL
- Click the Pencil icon next to Instance URL to edit and update it.
- Now you will see, Edit Instance URL form. In that form you can edit the instance URL, add headers specific to the instance and click on "Test Reachability" button to initiate the reachability testing
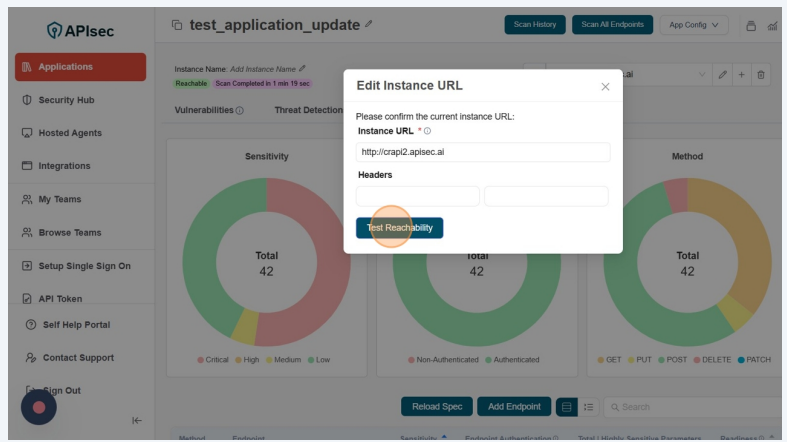
- After reachability test, you can observe the instance url changes in the screen along with the reachability status.
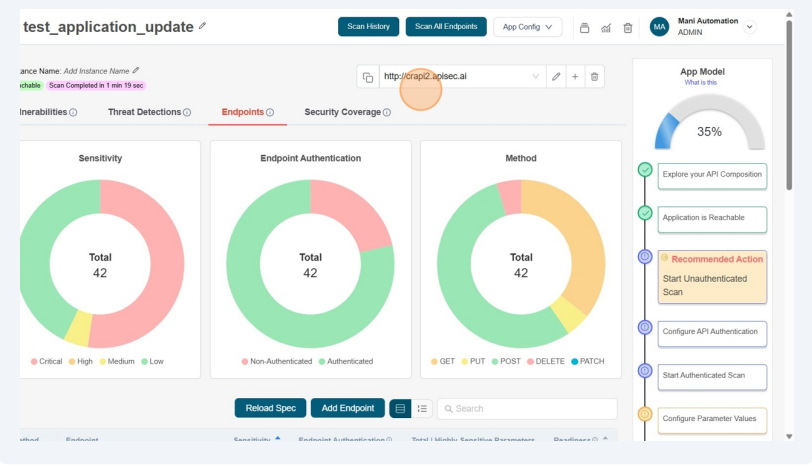
Users with View permissions cannot Edit instance URL in shared application
Adding instance URL
- Click the Plus (+) icon next to Instance URL to Add new instance url.
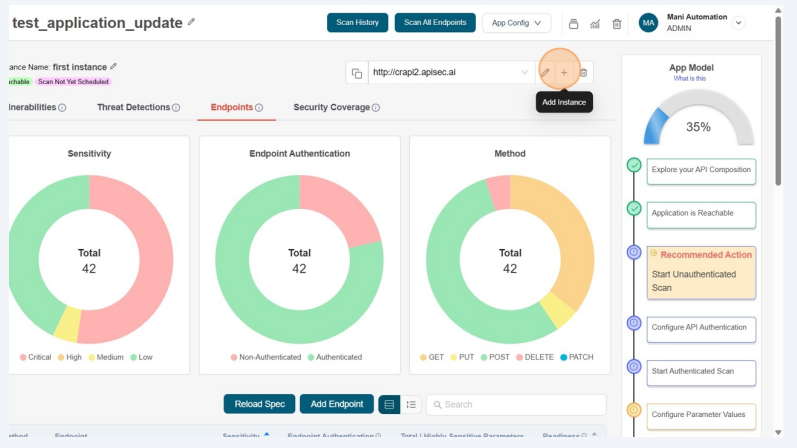
-
In the Form, enter Instance URl, instance name which is optional and click on the "Add" button.
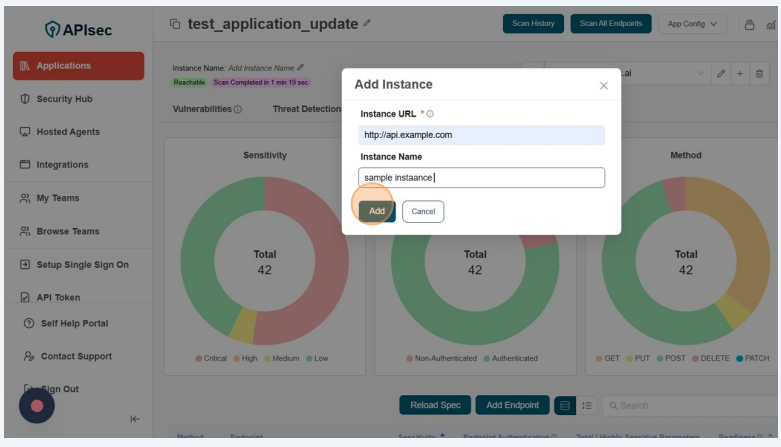
-
After that you can observe the newly added instance url in the screen along with its reachability status.
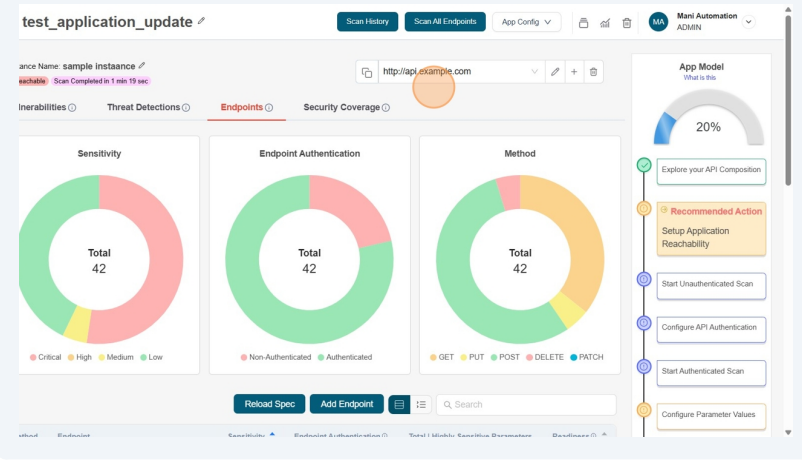 note
noteUsers with View permissions cannot add instance URL in shared application
Delete Instance
- Click the "delete" icon next to Instance URL to delete the instance url.
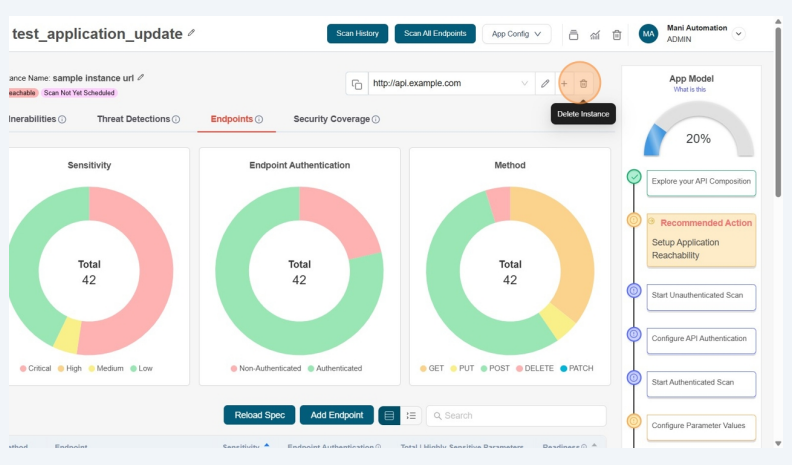
Users with View permissions cannot delete instance in shared application
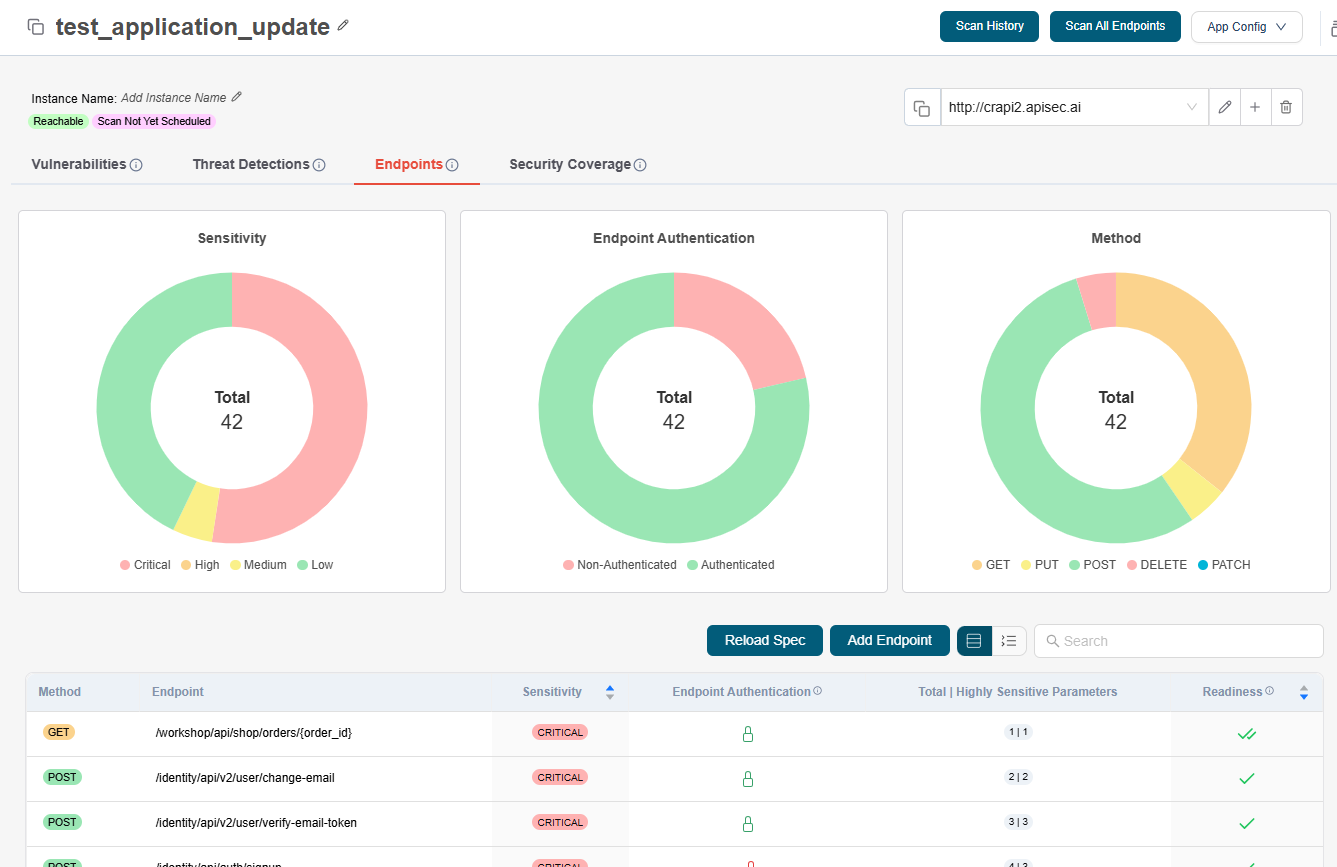
Endpoints
The Endpoints tab, helps you explore the full composition of your application, giving you clarity on every API endpoint in use. Instantly identify where sensitive data is being handled, monitor authentication coverage, and detect unauthenticated or high-risk endpoints.
With interactive dashboards and detailed endpoint reports, you can:
-
Classify APIs by sensitivity level (Critical, High, Medium, Low)
-
Track authentication status across all endpoints
-
Analyze API methods (GET, POST, PUT, DELETE, PATCH) at a glance
- Endpoint Parameter Configration
To change or customize request parameters, headers, query parameters for any endpoint
- Click on the seleted Endpoint
- To change Parameter configuration, click Pencil icon adjacent to the parameter.
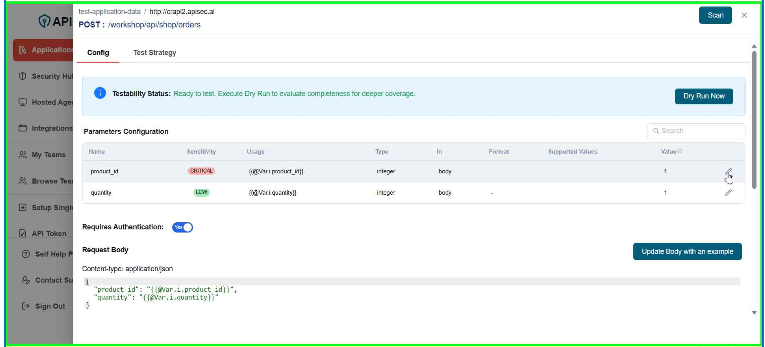
- Enter the details
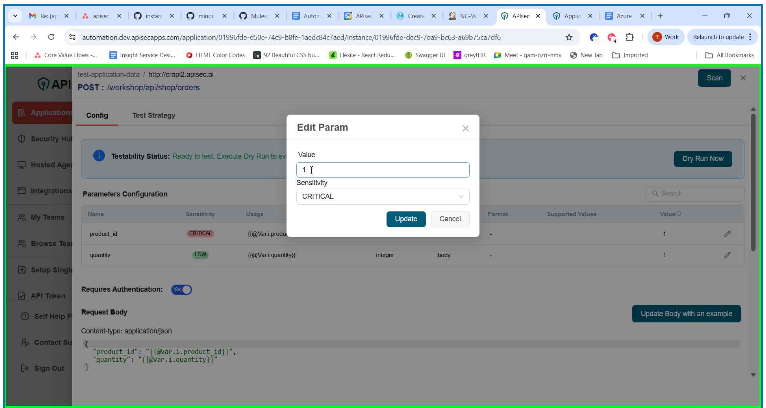
- Click Update
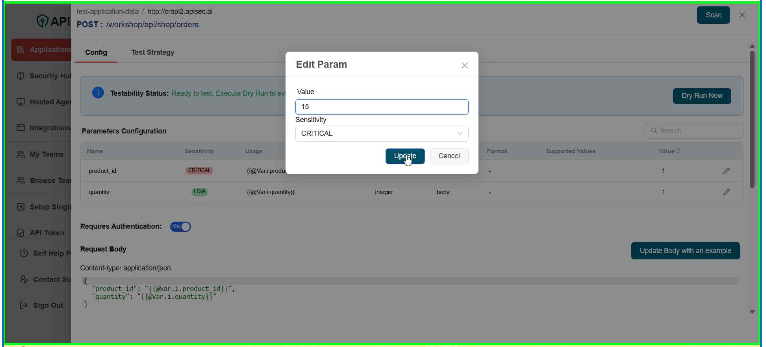
user role with View permissions can not change parameter configuration in shared application.
- To change Request body, click Update Body with an example.
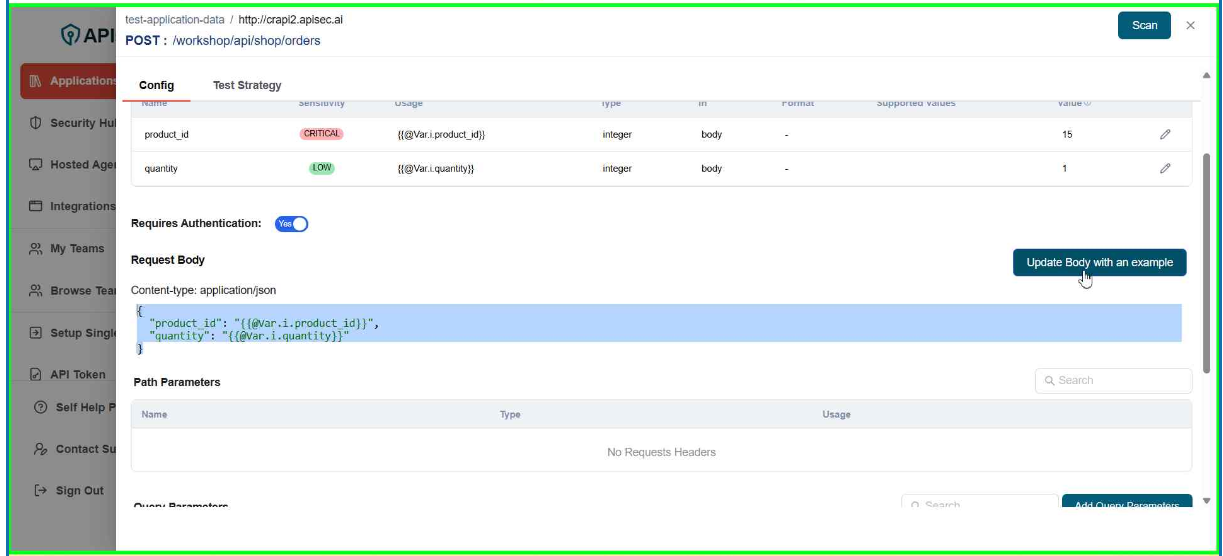
- Enter the sample data and Click Update
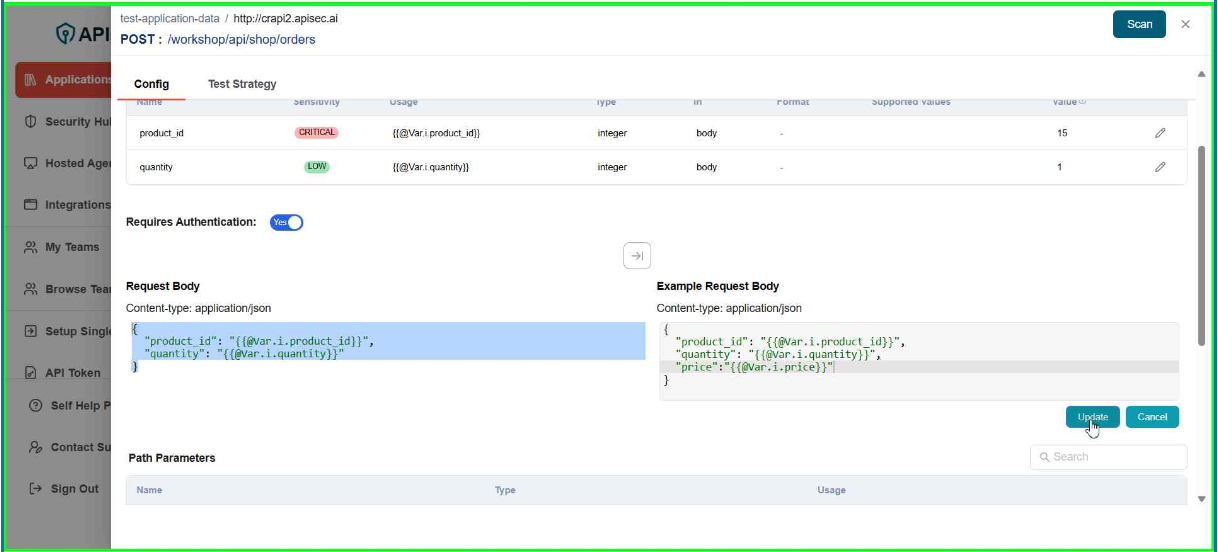
- Check updated request body
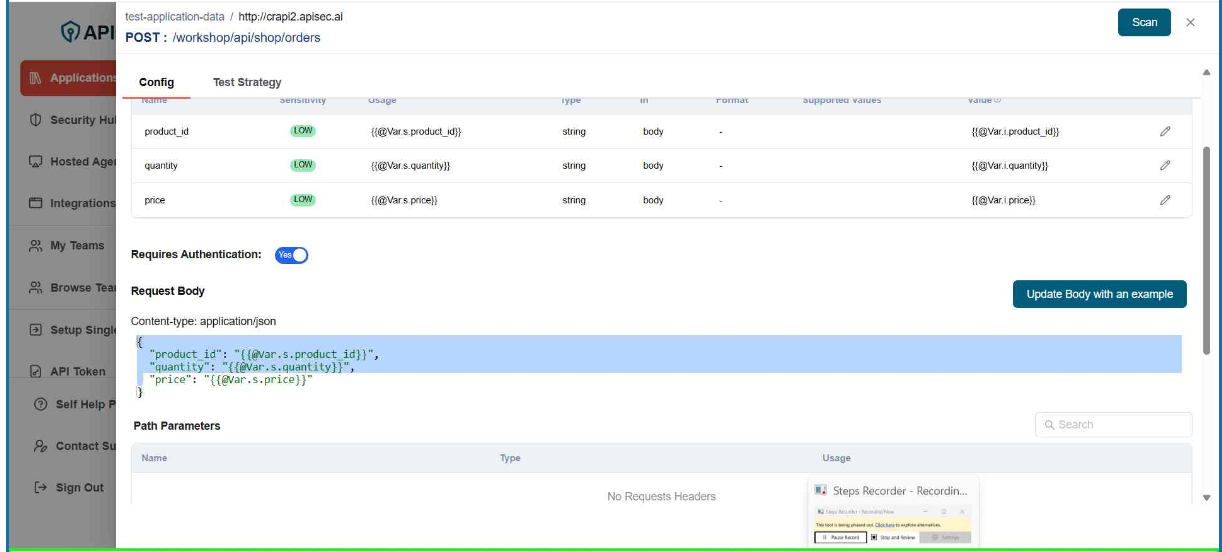
user role with View permissions can not change request body in shared application.
- To Add Query Parameter, click Add Query Parameters.
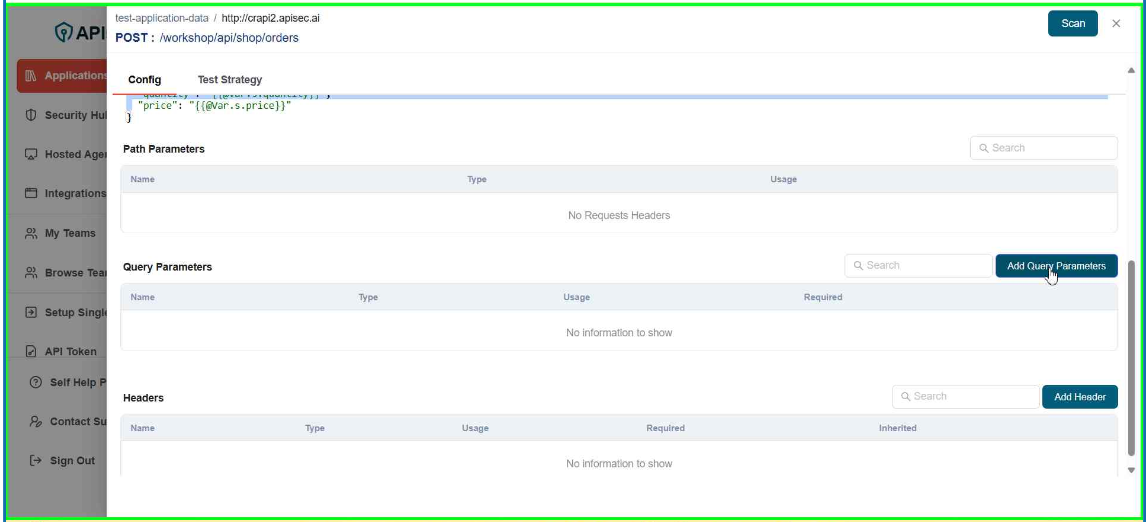
-
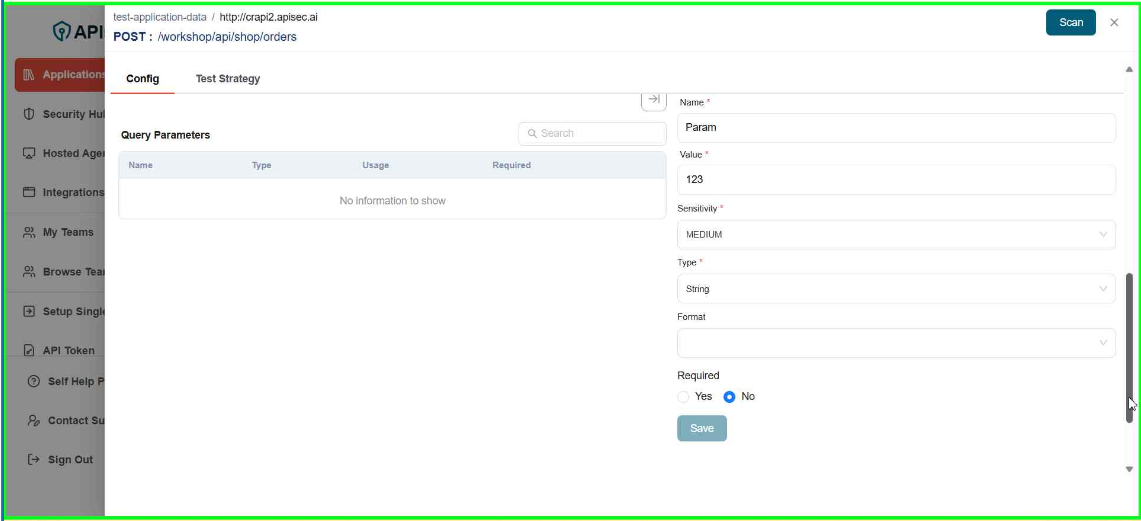
Enter the data:
- Name – The key of the query parameter (e.g., status, userId).
- Value – The assigned value for the parameter.
- Sensitivity – Classifies the parameter based on data sensitivity (Critical, High, Medium, Low).
- Type – Defines the data type of the parameter (string, number, boolean, etc.).
- Format – Specifies the expected format (e.g., email, UUID, date-time).
- Required – Indicates whether this parameter is mandatory for the request.
- Click Save
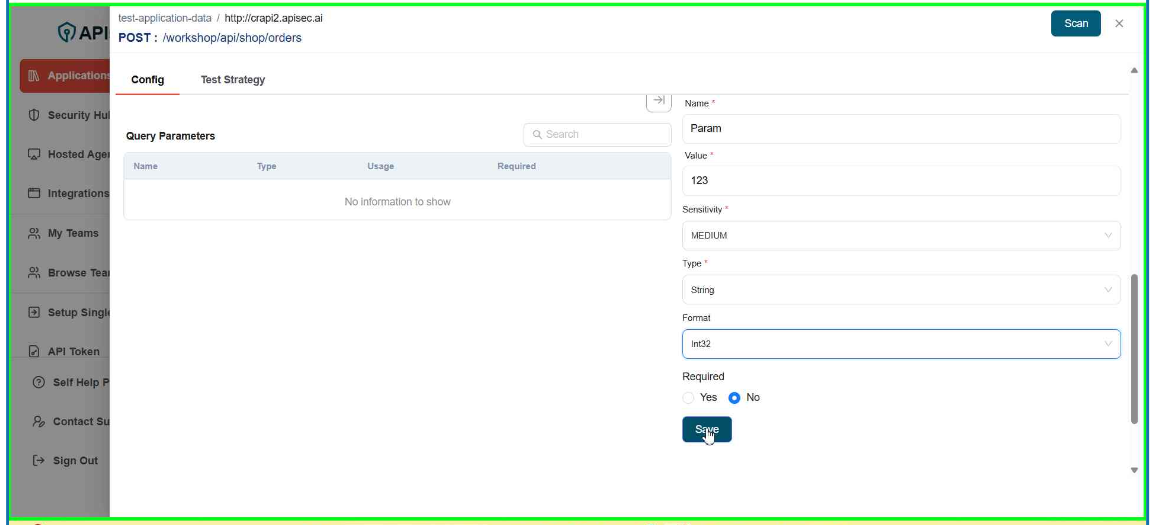
- Check newly added Parameter
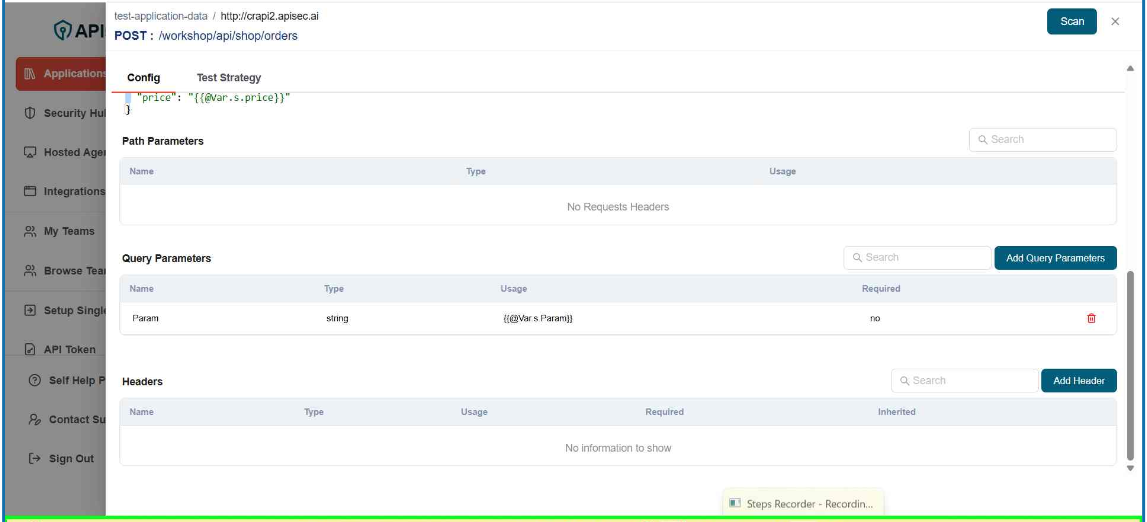
user role with View permissions can not add,edit and delete query parameter in shared application.
- To Add Header, click Add Header.

-
Enter the data:
- Name – The header key.
- Value – The value assigned to the header.
- Sensitivity – Classifies the header based on data sensitivity (Critical, High, Medium, Low).
- Required – Indicates whether this header must be included in the request..
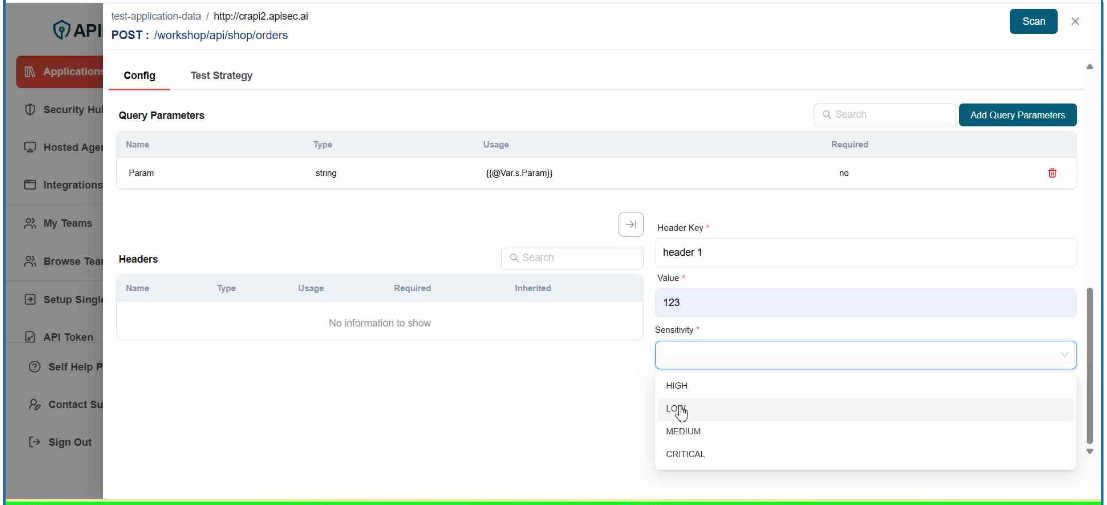
- Click Save
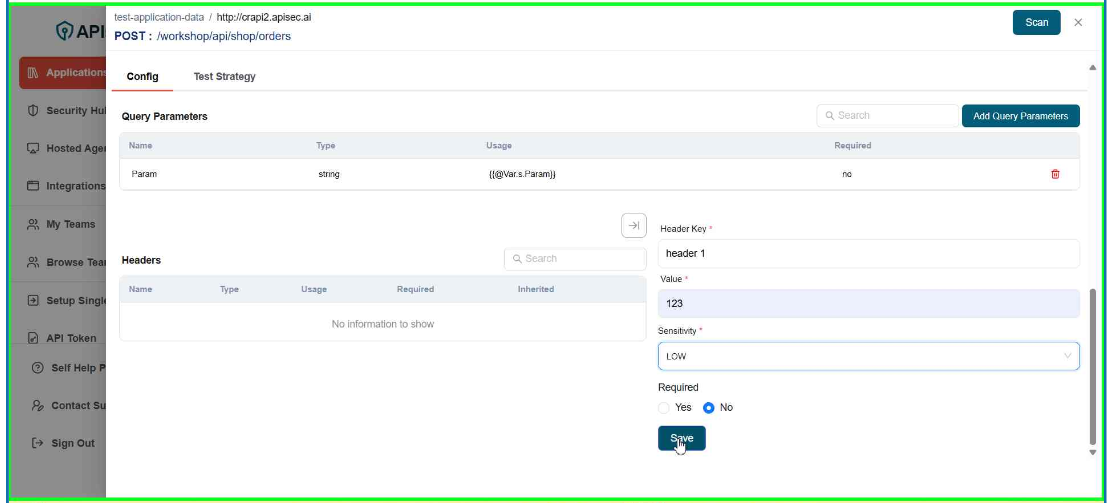
- Check newly added header
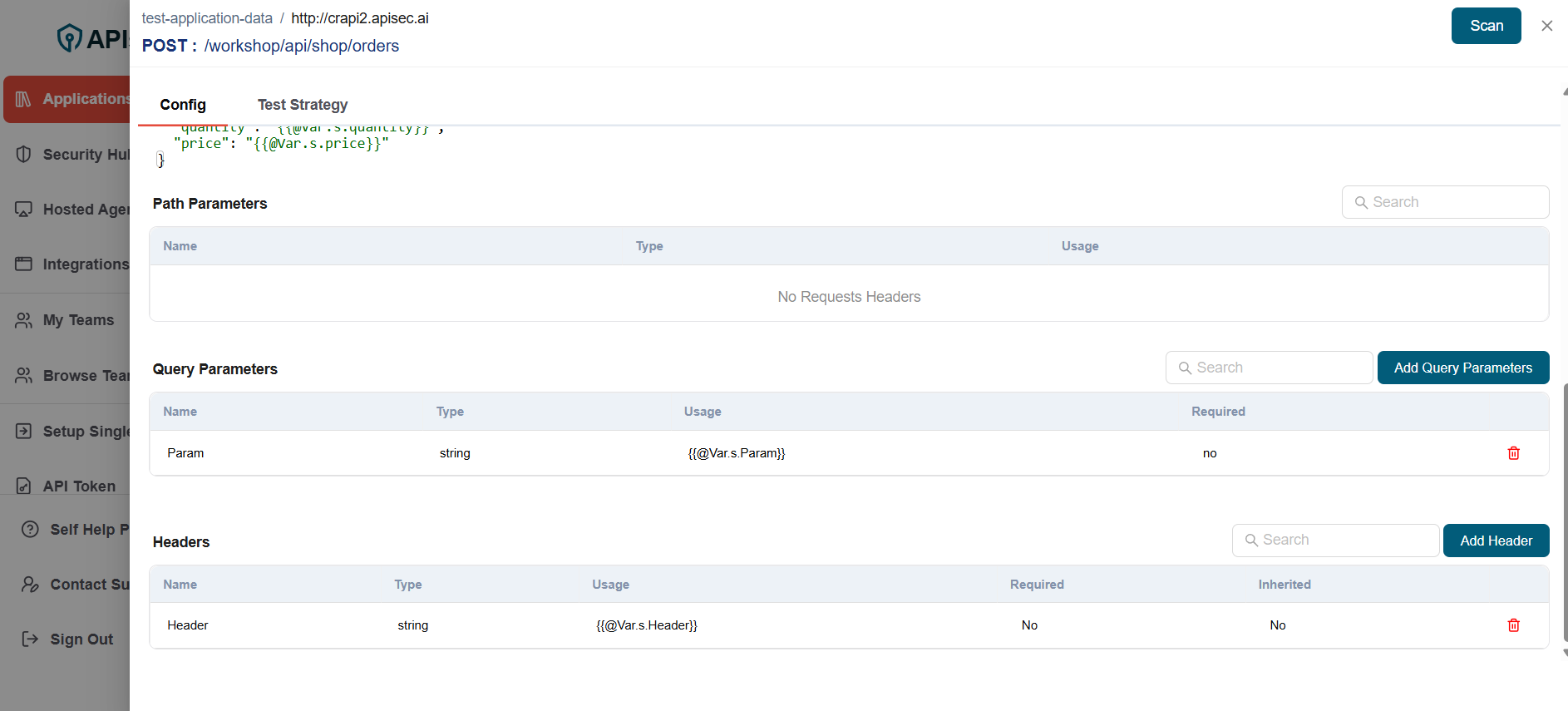
user role with View permissions can not add, edit and delete header in shared application.
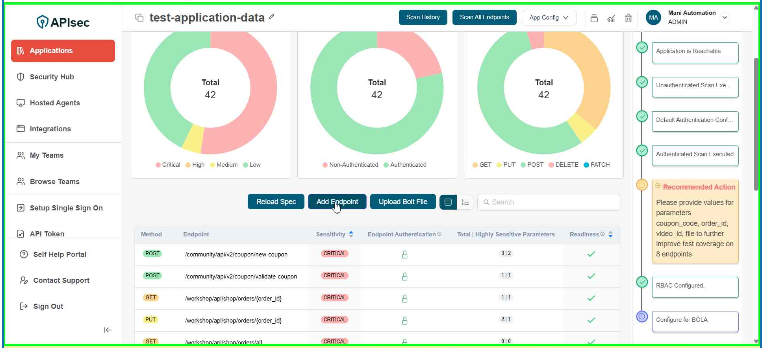
- Add Endpoint
The Add Endpoint allows you to manually register new API endpoints for an existing application. This is useful when certain endpoints are not automatically discovered or need to be explicitly defined for monitoring.
-
Click Add Endpoint
-
Select HTTP Method
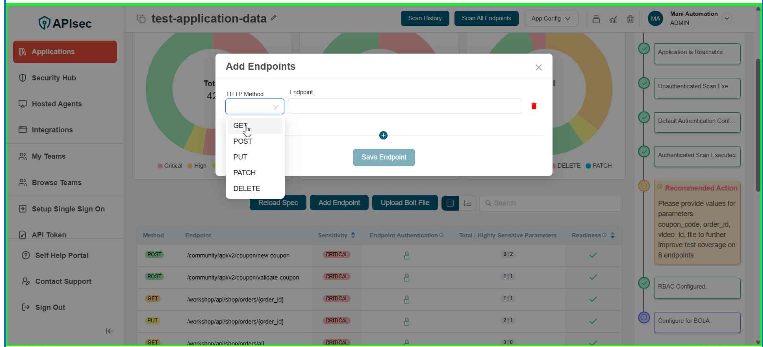
-
Enter Endpoint
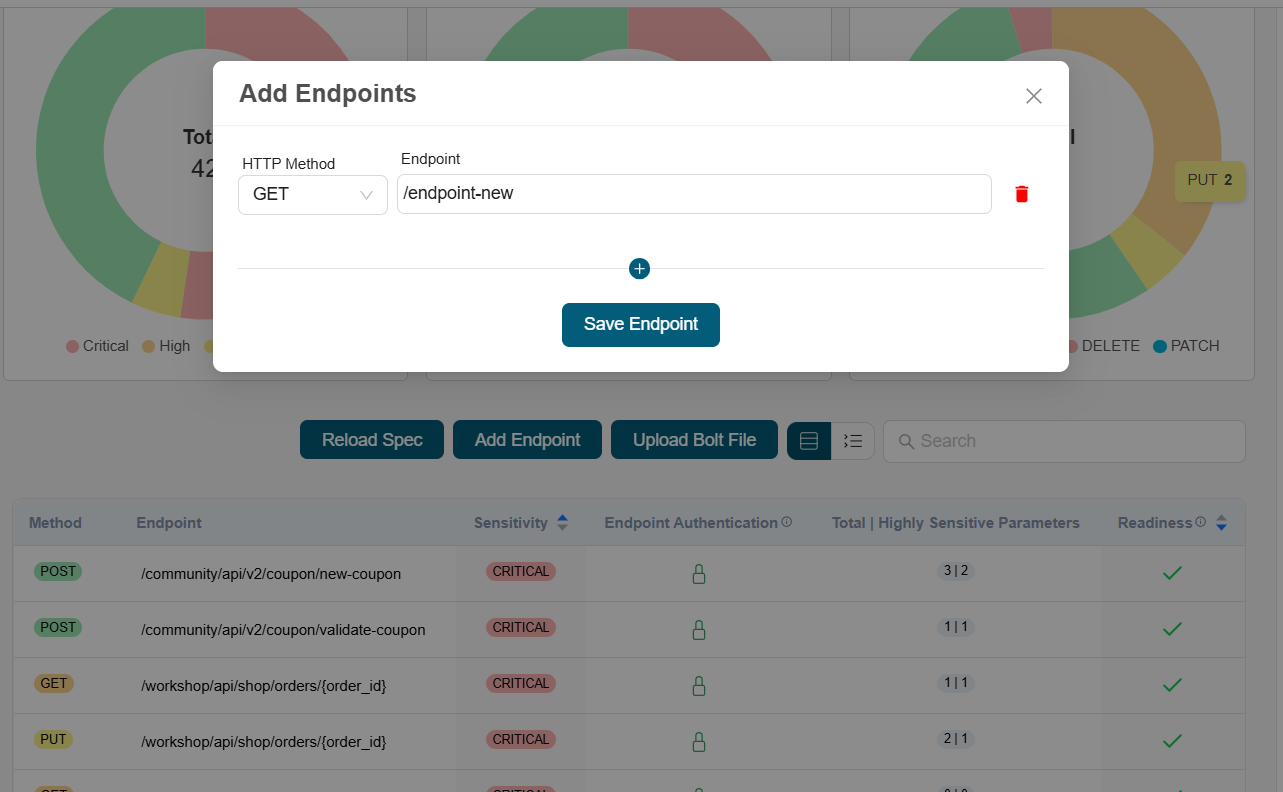
-
Click Save Endpoint
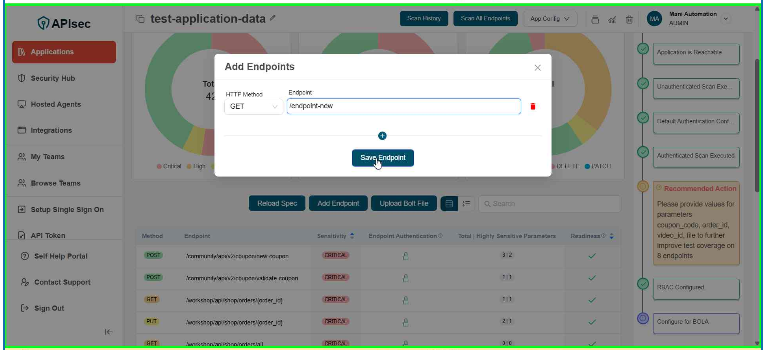
user role with View permissions can not add endpoints in shared application.
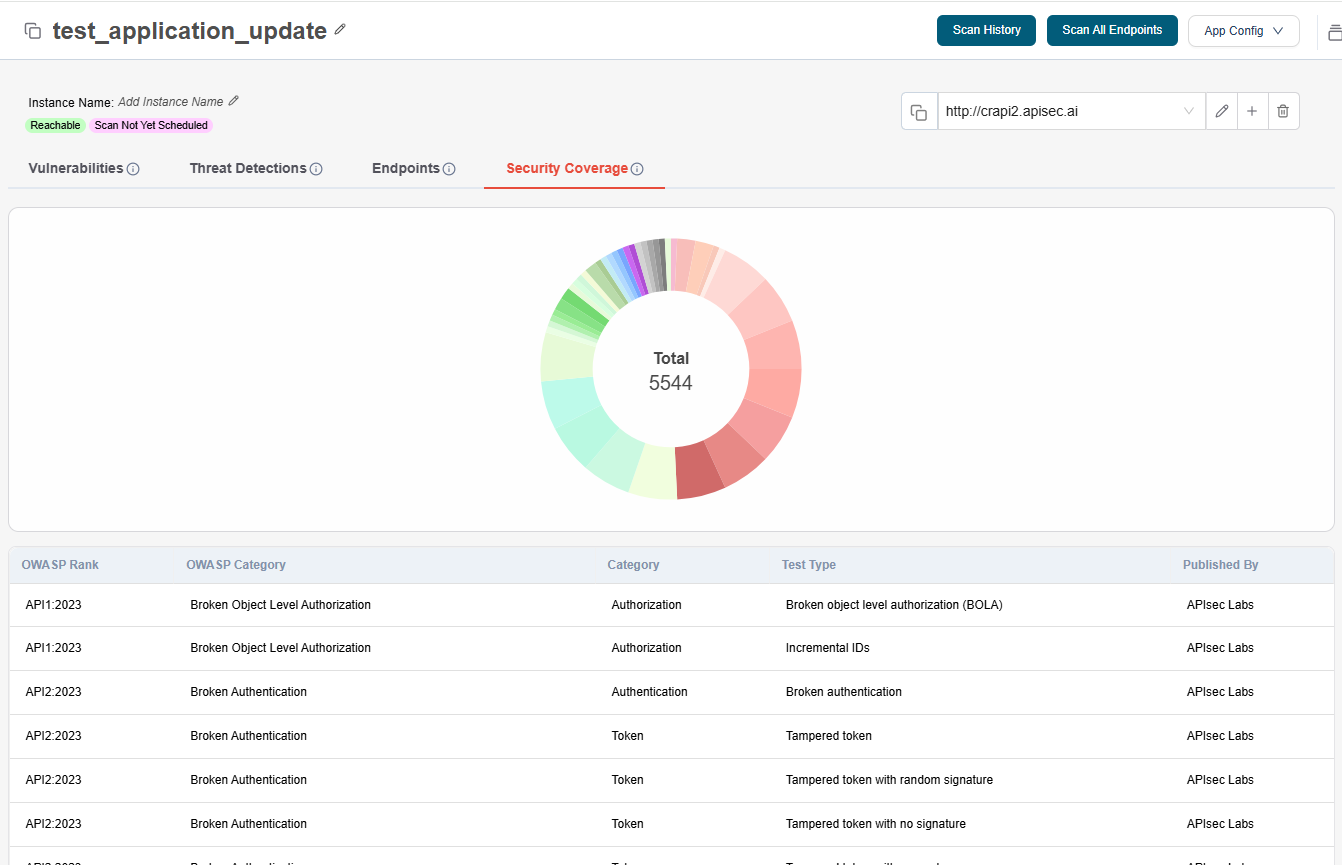
Security-coverage
Security Coverage provides a complete view of the tests safeguarding your APIs.
When you register an application, our platform automatically generates a custom suite of security tests aligned with the latest OWASP API Security Top 10 standards.
With Security Coverage, you can:
-
View the full suite of generated tests for your application
-
Understand the attack vectors your APIs are protected against
-
Track categories such as Authorization, Authentication, and Token Security
-
Detect risks like Broken Object Level Authorization (BOLA), Broken Authentication, Tampered Tokens ... and so on
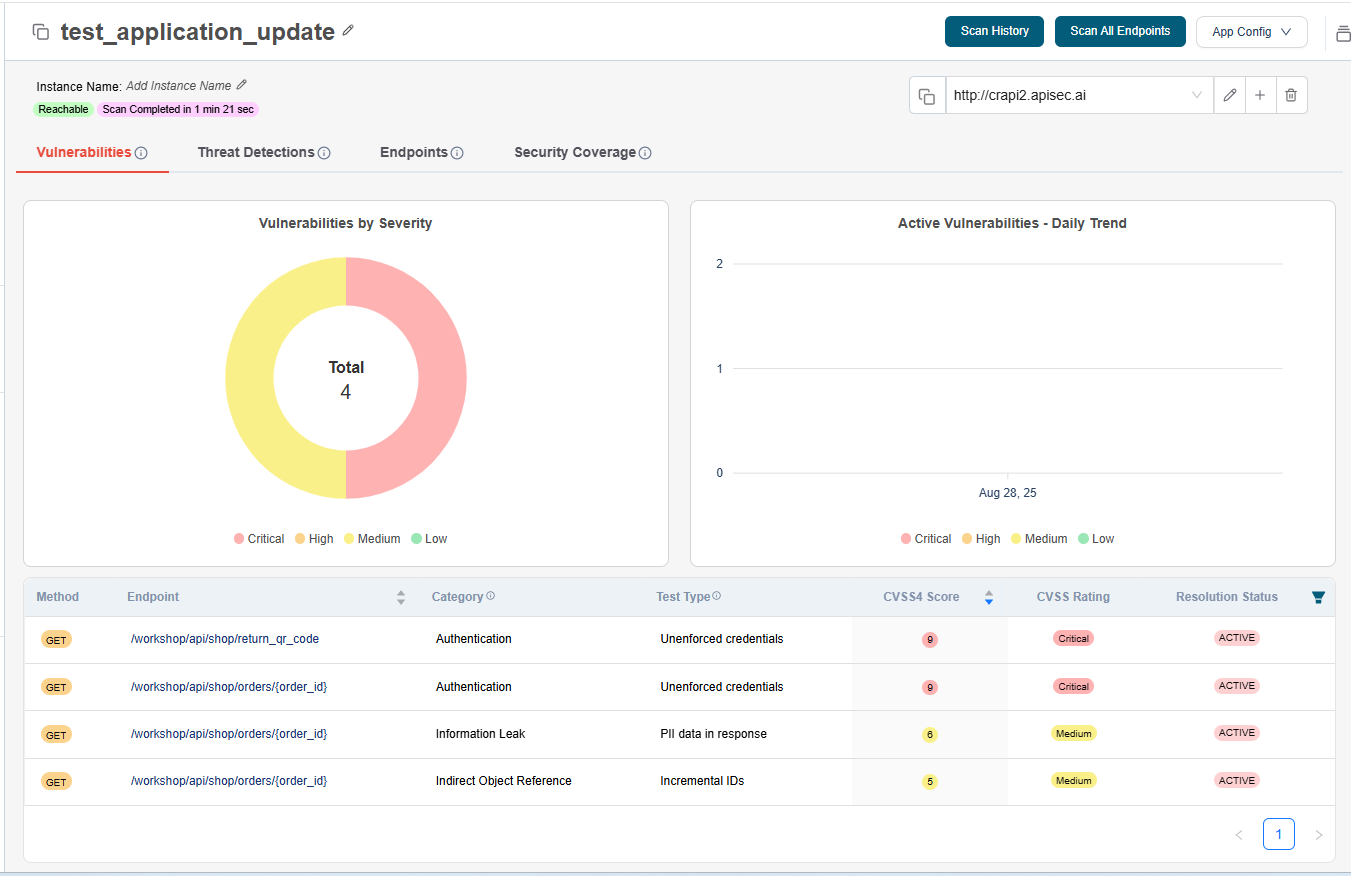
Vulnerabilities
After scanning endpoints, in Vulnerabilities tab you can find the detected security risks with detailed evidence and remediation steps to help you fix issues faster.
When scans detect potential security risks, our platform automatically generates detailed Vulnerability reports. Each entry includes:
-
Specific details of the vulnerability
-
Evidence of detection for validation
-
Remediation steps to guide quick fixes
With clear severity levels, CVSS scores, and resolution status, you can prioritize and address issues efficiently
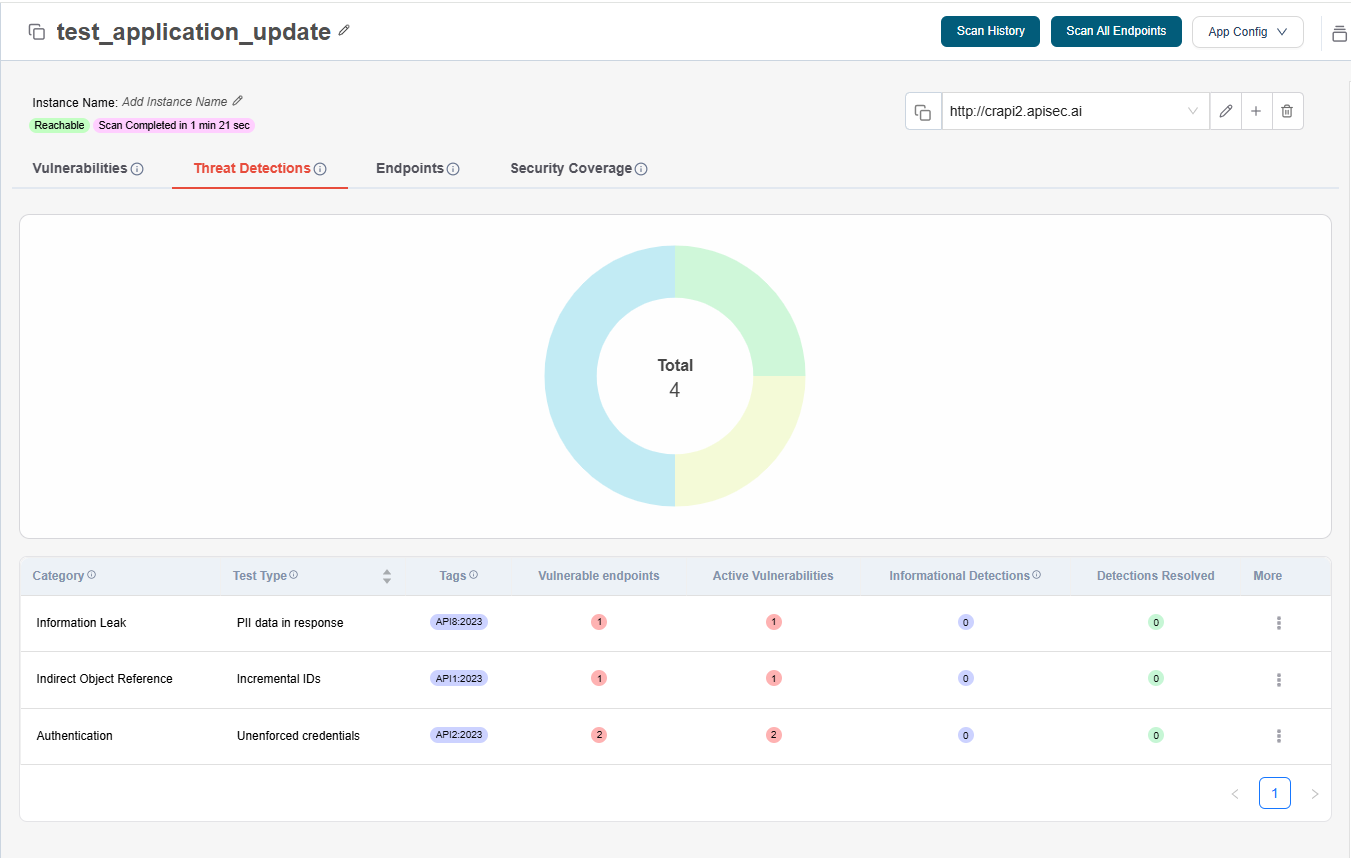
Threat Detection
Threat Detections show vulnerability types across your APIs and highlight endpoints affected by the same threats.
-
Identify vulnerability types present in your APIs
-
See which endpoints share the same vulnerability patterns
-
Understand how threats propagate across your application
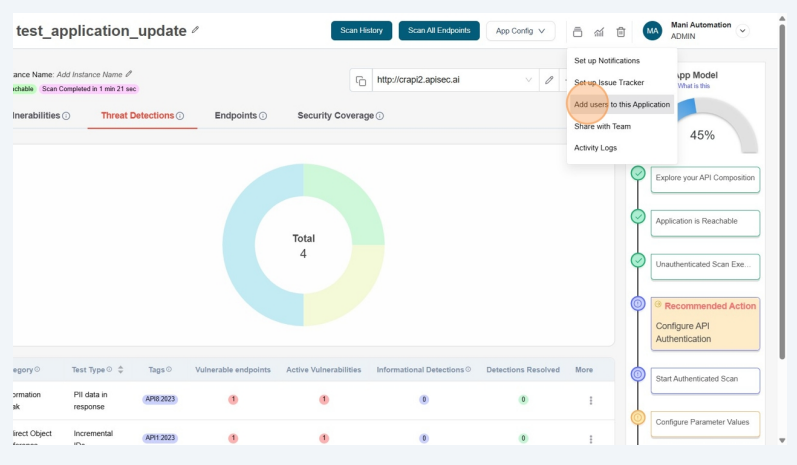
Add users to this application
This option enables you to add users to the application by specifying their email and assigning appropriate access permission.
-
Click on "Administration" menu icon in the top bar.
-
-
From the drop down select "Add users to this Application" menu option
-
-
In the Users form, enter the user's email address and select the access permission (View or Edit).
-
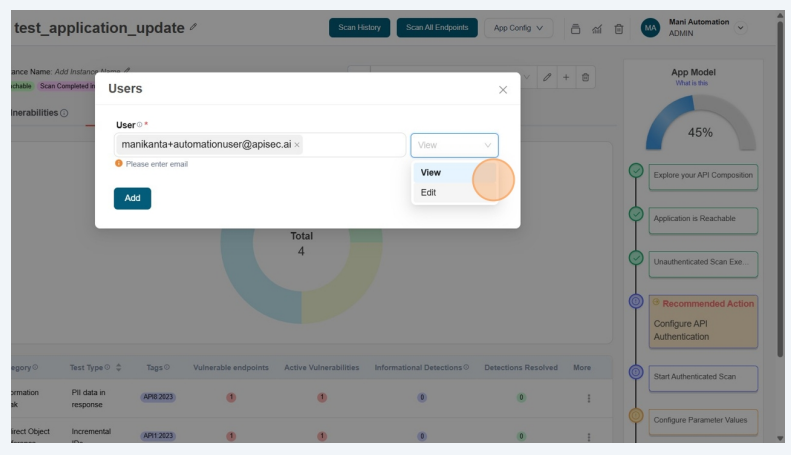
- For SSO users, the system displays an SSO tag beside the email address in the auto-complete options.
- Users with View permissions cannot share a shared application.
-
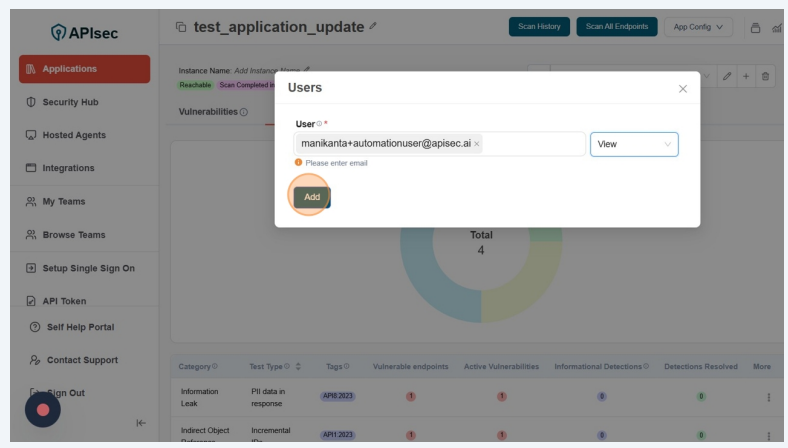
Click on "Add" button
-
-
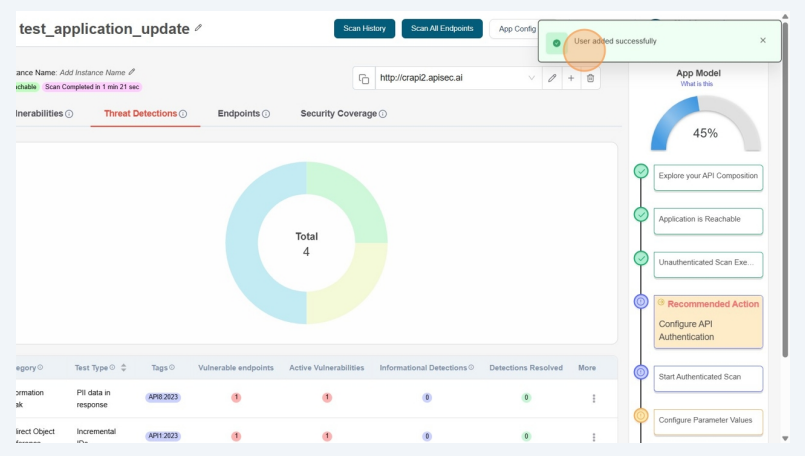
Now the user can access this application.
-
Share with Team
As the admin or owner of the application, you can use this option to share the application with a specific team. Team members will then be able to access the application and perform activities based on their permission.
- Click on "Administration" menu icon in the top bar.

- From the drop down menu, select Share with Team
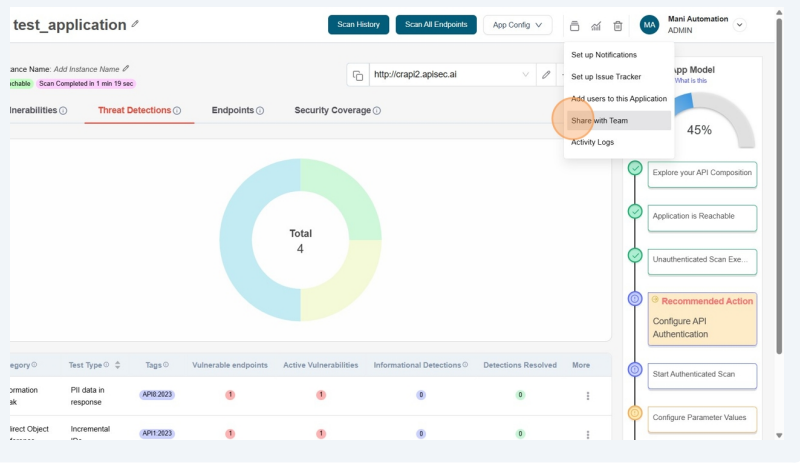
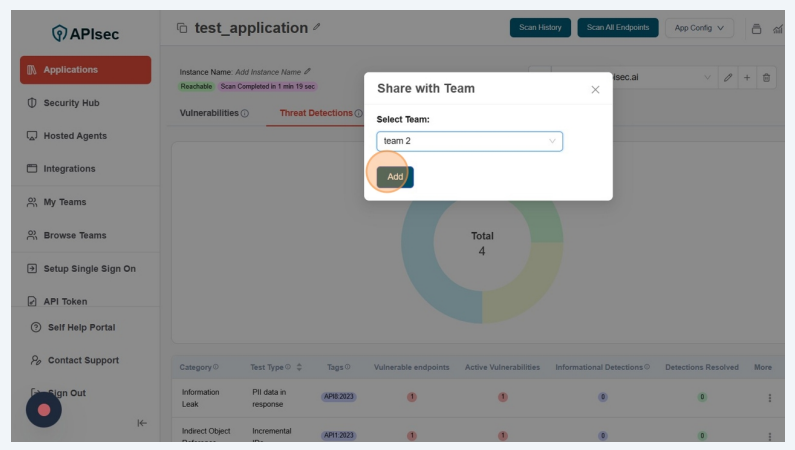
- Select team and click on the "Add" button
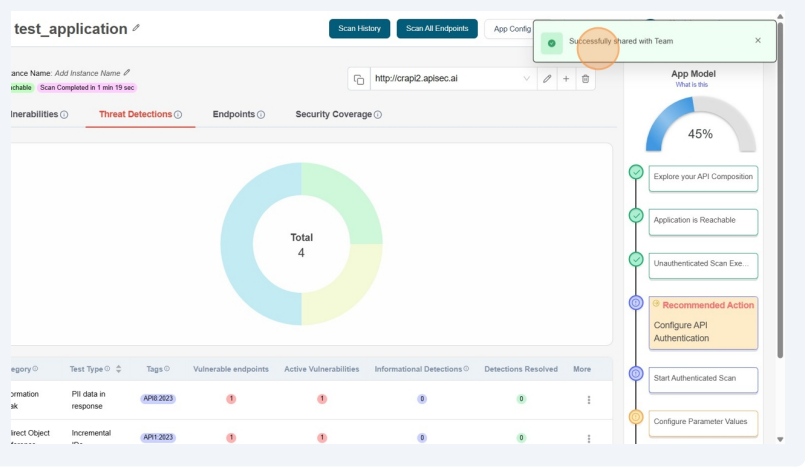
- Now the Team members can access the application.
Delete Application
- Click the "Delete" icon in the top menu bar to remove the application.
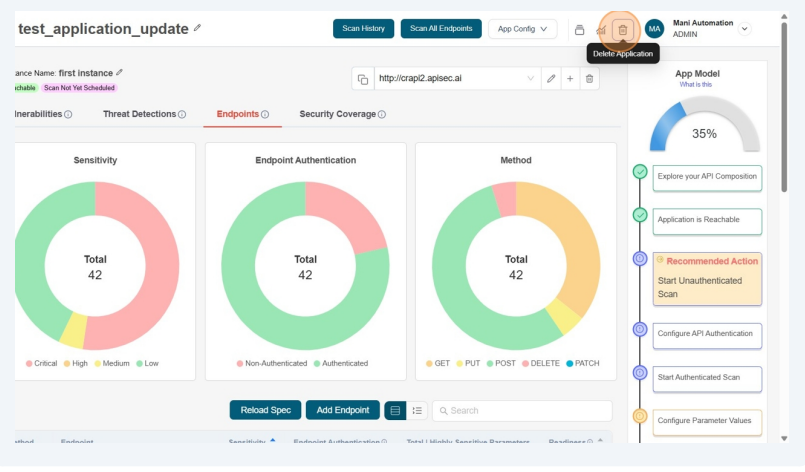
Users with View permissions cannot delete shared application
After onboarding, ensure the API is secured by enabling authentication mechanisms such as OAuth or API keys.
For a step-by-step guide, check out:
- How to Onboard an Application Using OpenAPI Spec
- By following these structured steps, you can efficiently onboard APIs while maintaining high standards of security and documentation.