Overview: Viewing and Understanding Vulnerabilities
What is Vulnerability Analysis in APIsec ?
Vulnerability analysis is a crucial part of API security testing. It provides insights into security weaknesses discovered during scans, helping teams prioritize and remediate potential threats. Viewing vulnerabilities within the APIsec platform allows users to assess risk levels, understand security gaps, and take action to improve API security posture.
How Are Vulnerabilities Presented?
- Graphical Representation of Vulnerabilities
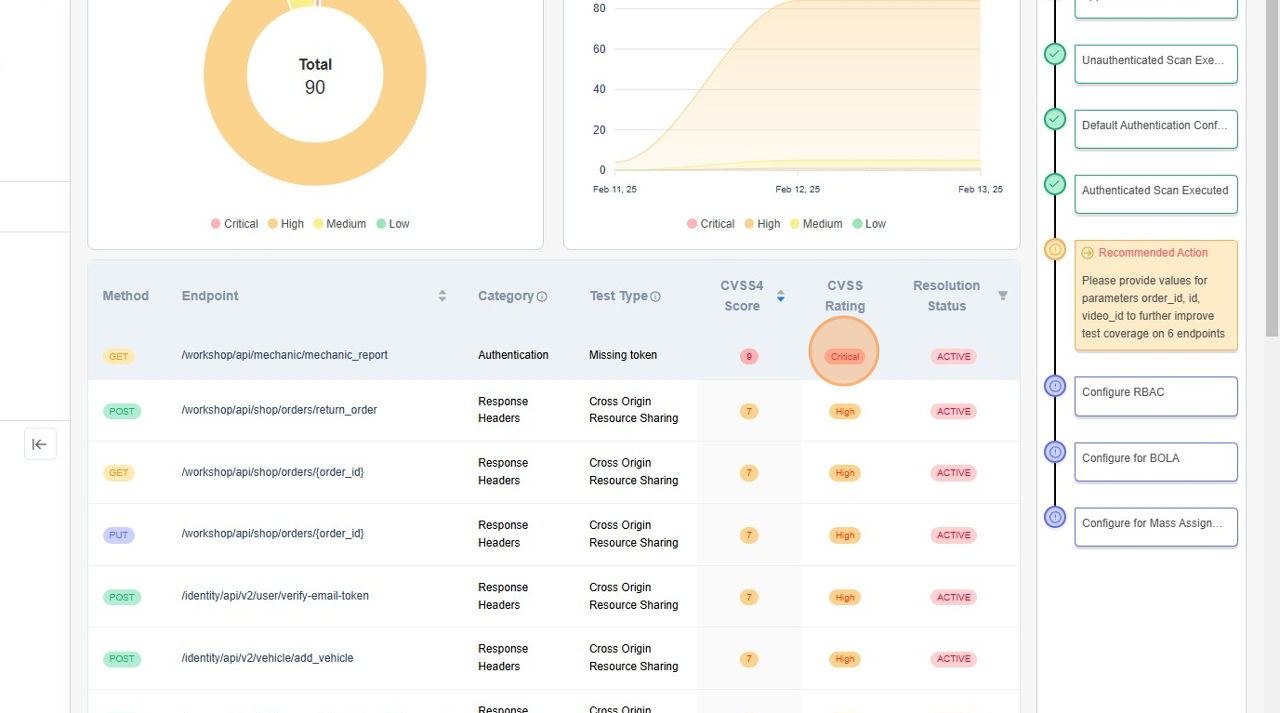
- The platform displays vulnerabilities using severity-based categorization (Critical, High, Medium, Low).
- A daily trend chart shows active vulnerabilities over time, helping teams track security posture changes.
- Detailed Vulnerability Table
- Each vulnerability is associated with an HTTP method and endpoint to indicate where the issue exists.
- Categories such as Authentication, Authorization, Response Headers, or Input Validation provide context on the security gap.
- The test type specifies the kind of security check that detected the issue (e.g., missing tokens, misconfigured headers, or broken access controls).
- A CVSS score helps assess the severity of each vulnerability, guiding remediation priorities.
- The resolution status indicates whether a vulnerability is active, mitigated, or pending review.
Why Is Viewing Vulnerabilities Important?
- Helps Prioritize Fixes Based on Severity
- Critical and high-severity vulnerabilities should be addressed first to reduce exposure.
- Medium and low-severity issues provide insights for long-term security improvements.
- Provides Context for Each Vulnerability
- By linking vulnerabilities to specific API endpoints, teams can quickly identify affected services.
- Categorization allows security teams to focus on key areas such as authentication, data exposure, or response security.
- Supports Compliance and Risk Management
- Visibility into API vulnerabilities ensures compliance with security frameworks like OWASP API Security Top 10.
- Historical trends allow teams to track security improvements over time.
Understanding the Vulnerability Details Page
- Header Section
- Displays the HTTP method (GET, POST, etc.) and the exact API endpoint affected.
- This helps developers locate and reproduce the issue efficiently.
- Vulnerability Breakdown
- Includes details about the type of risk, impacted API function, and recommended fix.
- Helps teams understand why the vulnerability exists and how to address it.
- Resolution Actions
- The platform provides recommendations on fixing misconfigurations, improving authentication, or updating access controls.
- Suggested configurations align with security best practices to prevent future issues.
Next Steps
- Click on a vulnerability row to access more details about the issue.
- Review affected endpoints and associated risks.
- Use provided resolution steps to apply security fixes.
- Re-scan the API to verify that the vulnerability has been successfully mitigated.
By regularly reviewing vulnerabilities and taking corrective actions, teams can ensure ongoing API security, reduce attack surfaces, and strengthen compliance efforts
Navigate to URL
Open your browser and visit: https://<your-tenant>.apisecapps.com
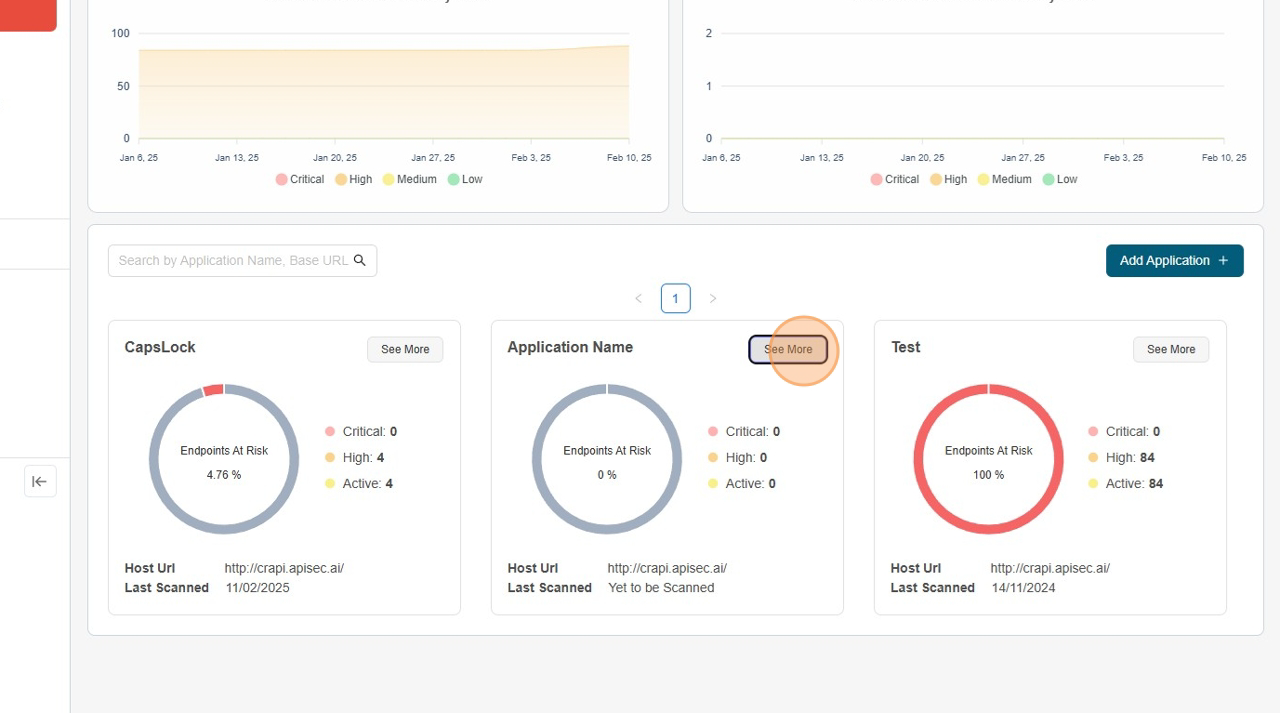
Visit the application
- Click on "See more" to open the application
Vulnerabilities Tab
It is assumed that you have already set up the app and performed either an Unauthenticated Scan or an Authenticated Scan. The vulnerabilities have been identified for you through the APIsec scan.
- Click Vulnerabilities Tab
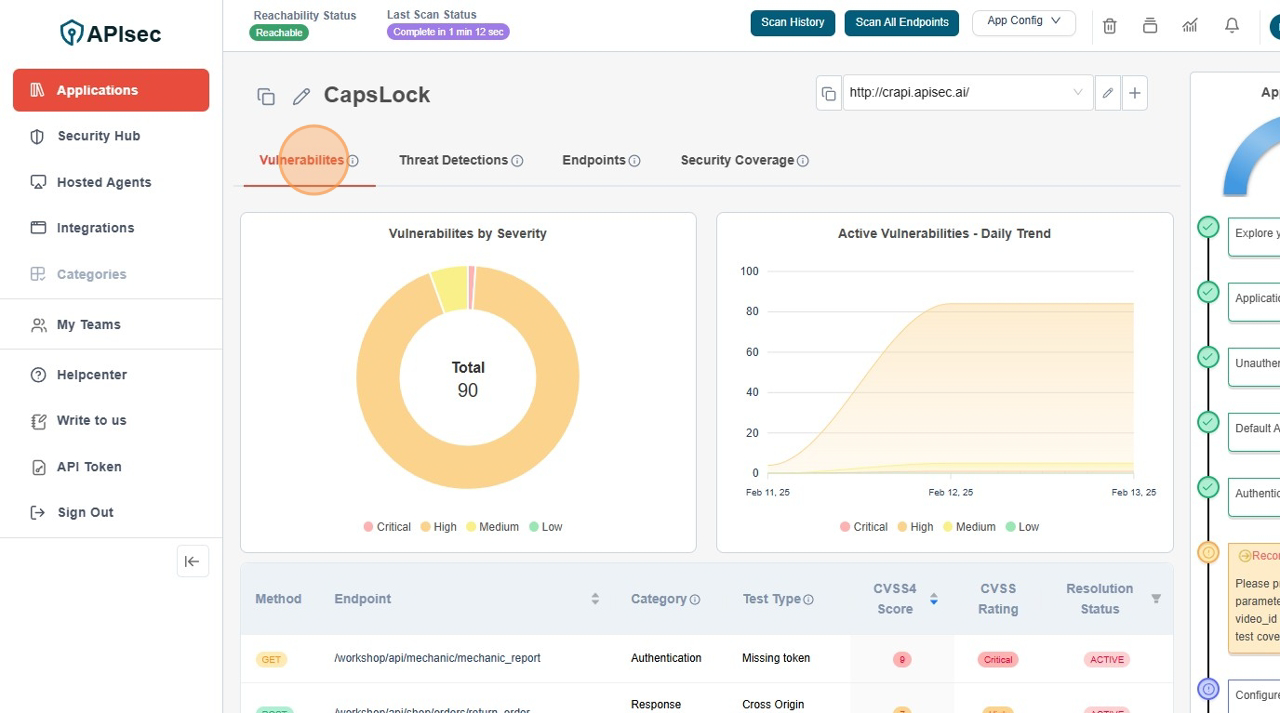
This provides information about the vulnerabilities discovered by the APIsec scan. It includes a graphical representation of Vulnerabilities by Severity and Active Vulnerabilities - Daily Trend, comparing Critical, High, Medium, and Low severity vulnerabilities identified during the scan.
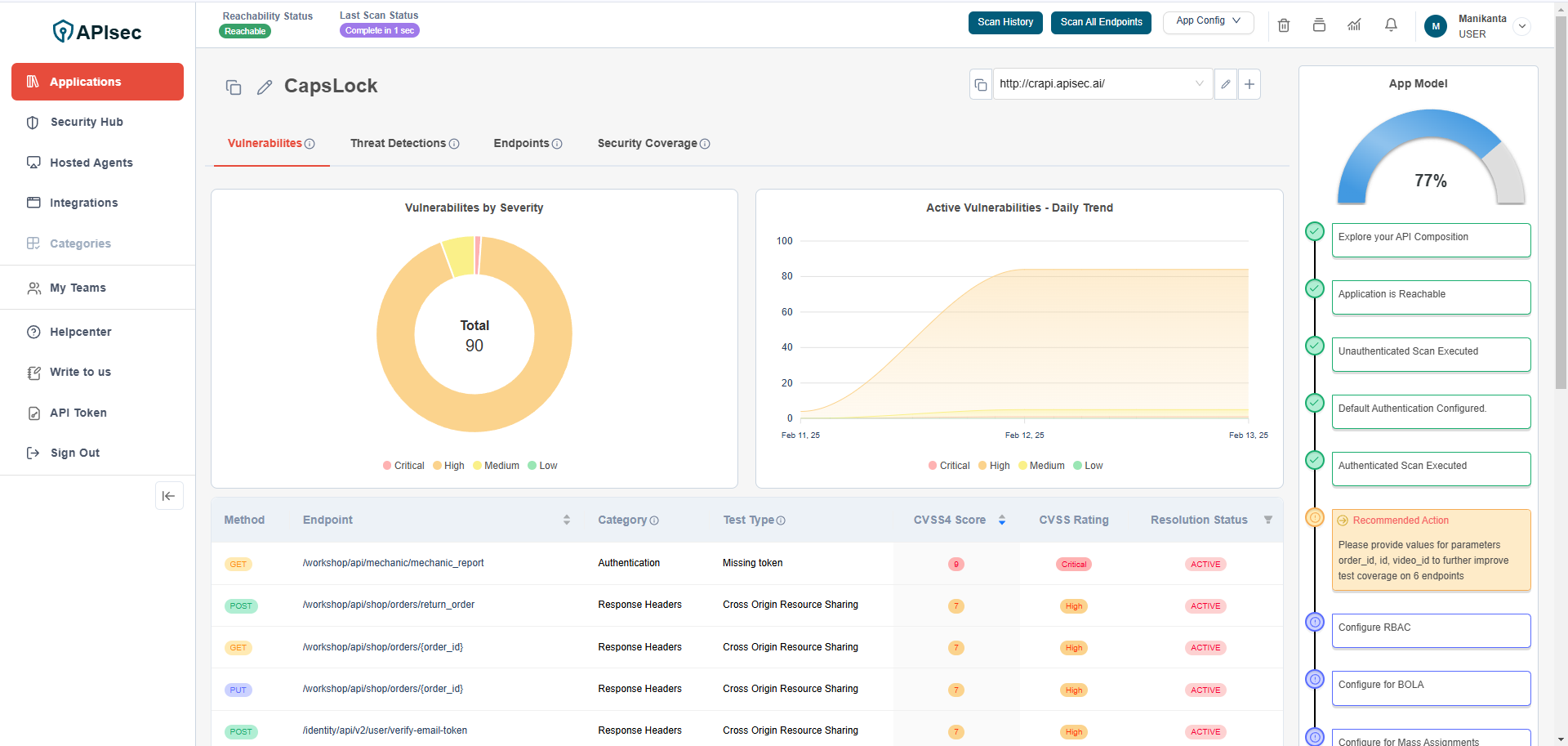
Check Vulnerability Details view
- Click on Vulnerability Row to get more details
Understanding of Vulnerability details page.
- Header section
- It shows the details of Method and URL endpoint
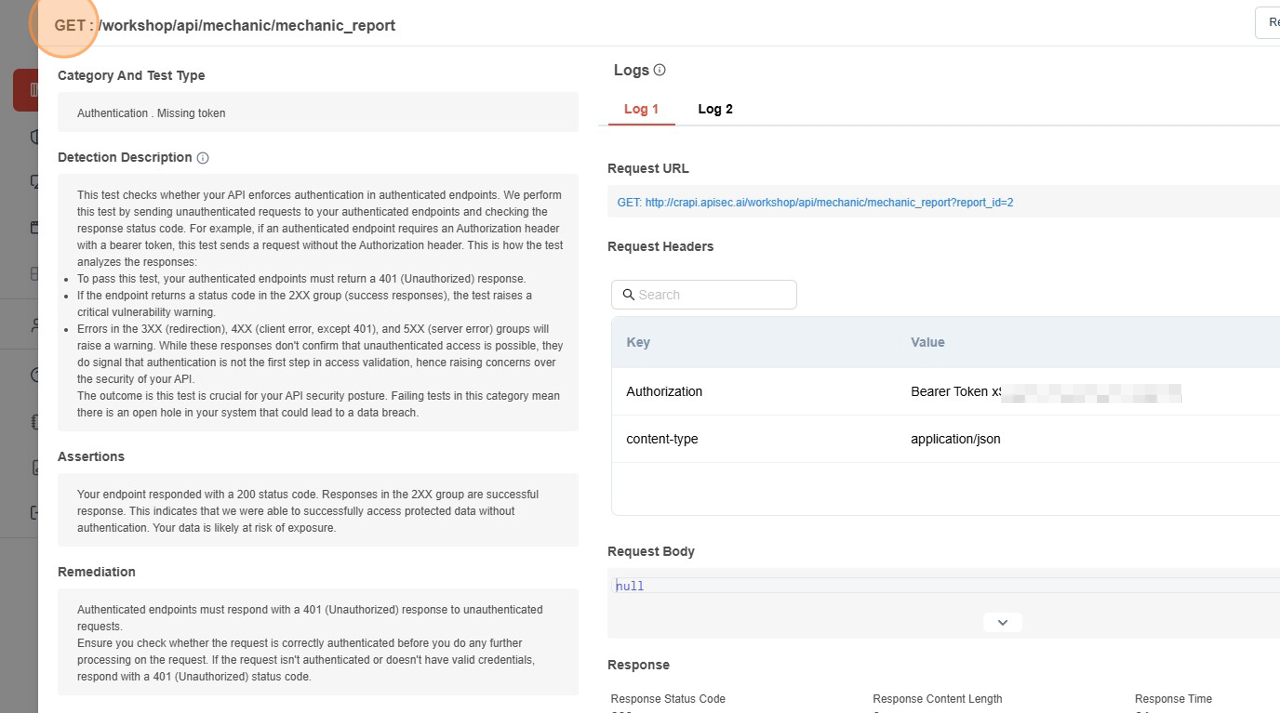
- It shows the details of Method and URL endpoint
- Logs
- It shows the detailed logs for each URL endpoint
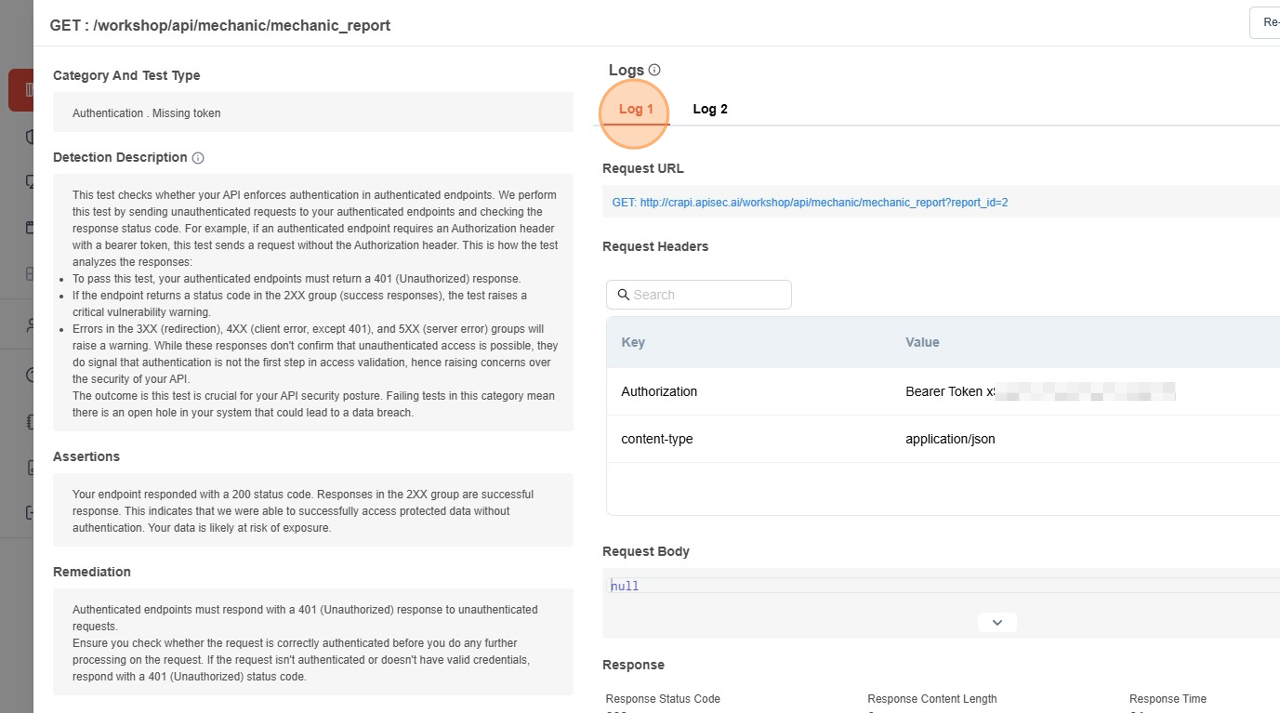
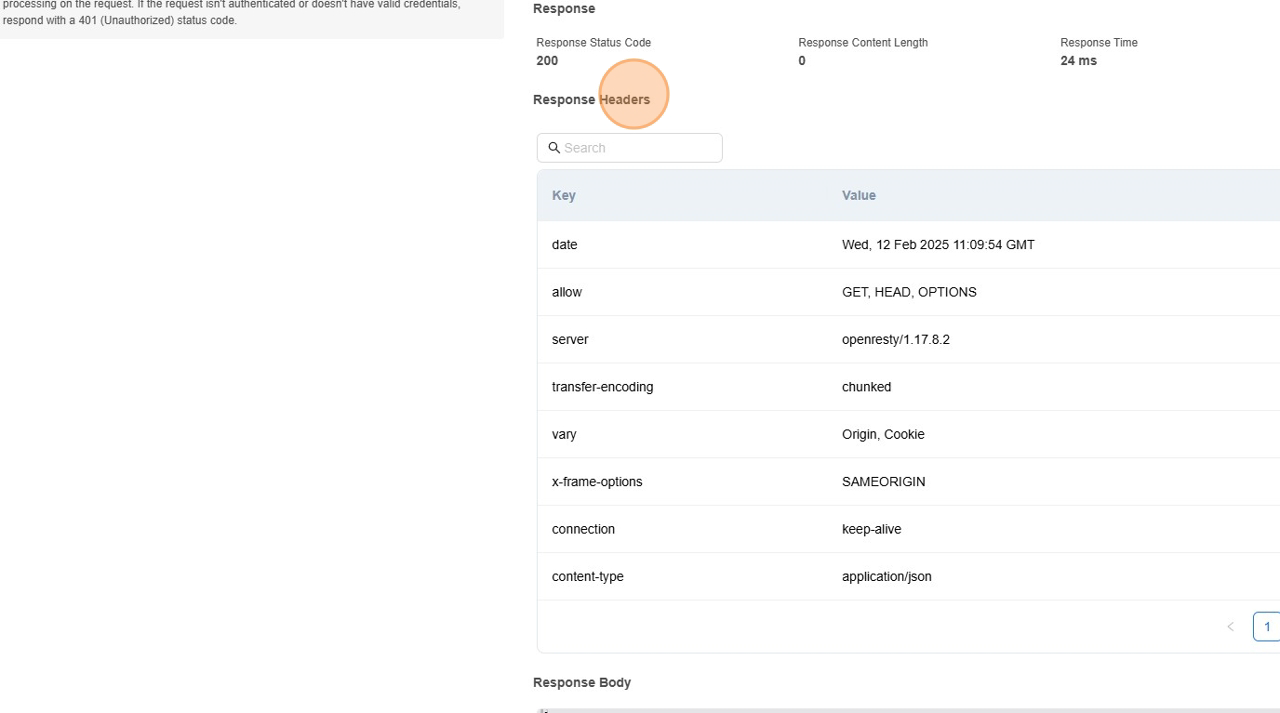
- It shows the detailed logs for each URL endpoint
- Raw view
- It also shows logs in Raw format. click on "Raw" button.
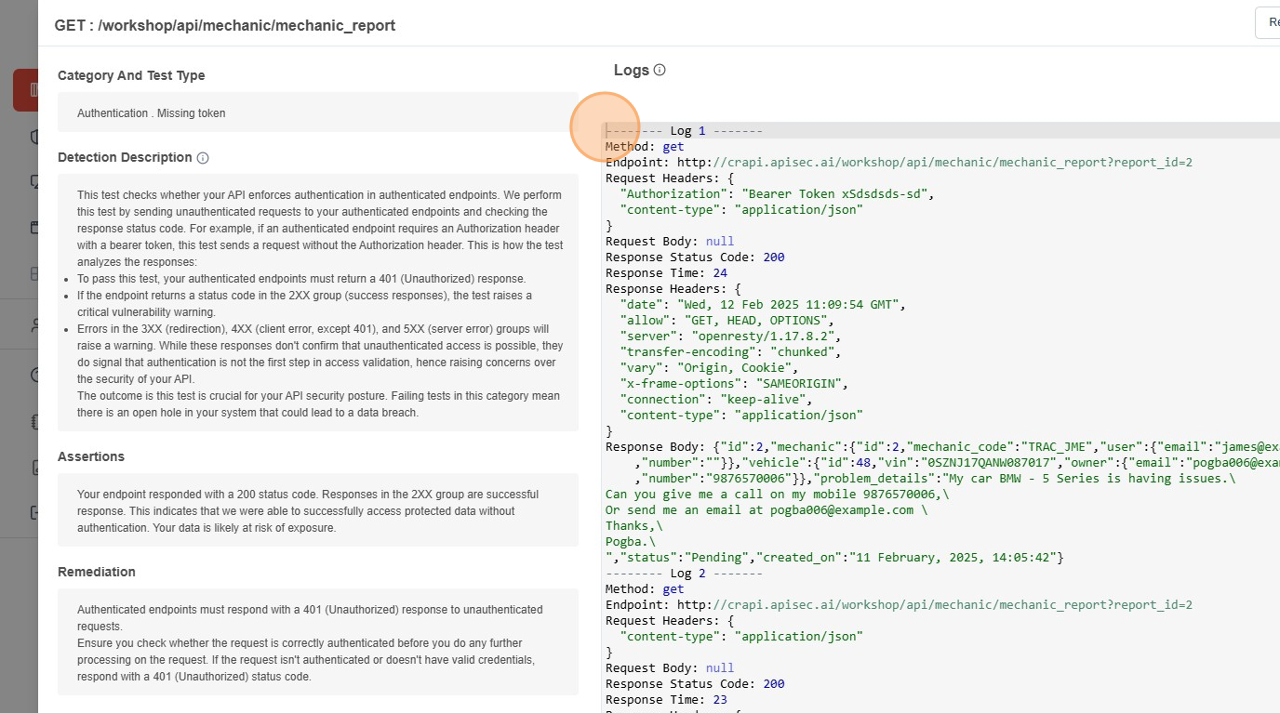
- It also shows logs in Raw format. click on "Raw" button.
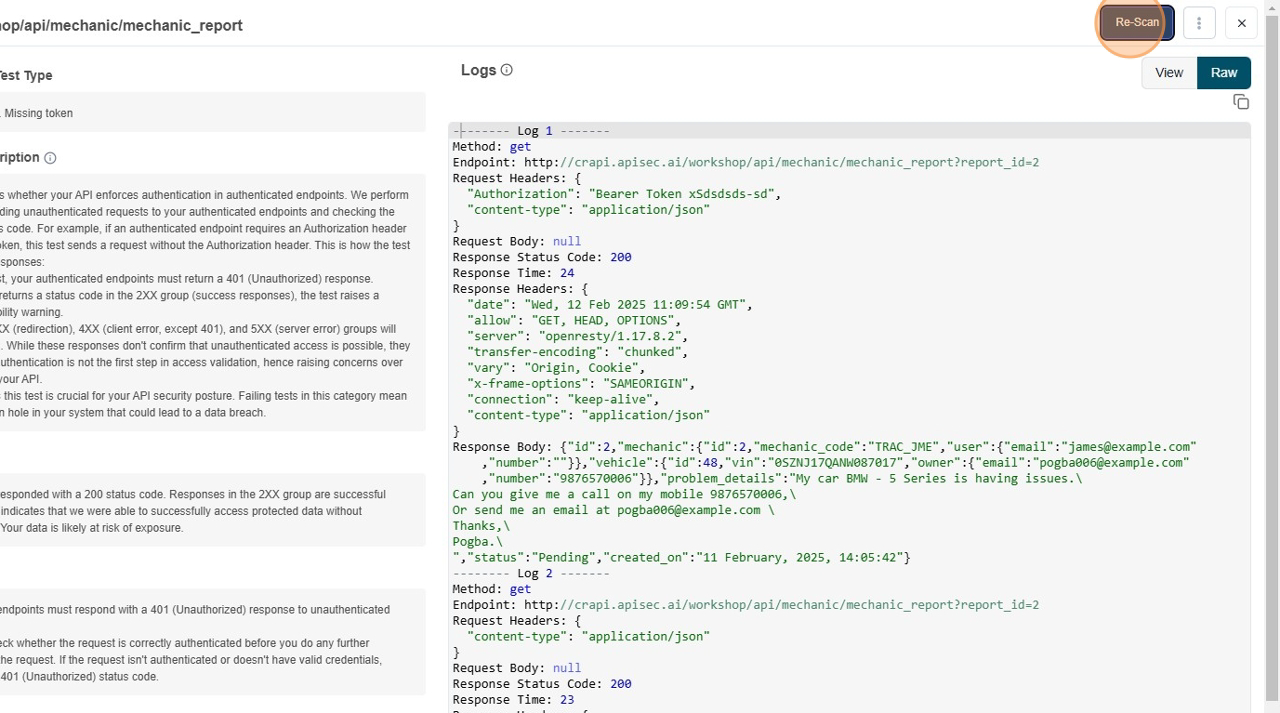
- Re-scan
- It provides the ability to initiate the Re-scan form the logs section.
- Click on Re-Scan
- Confirm Scope
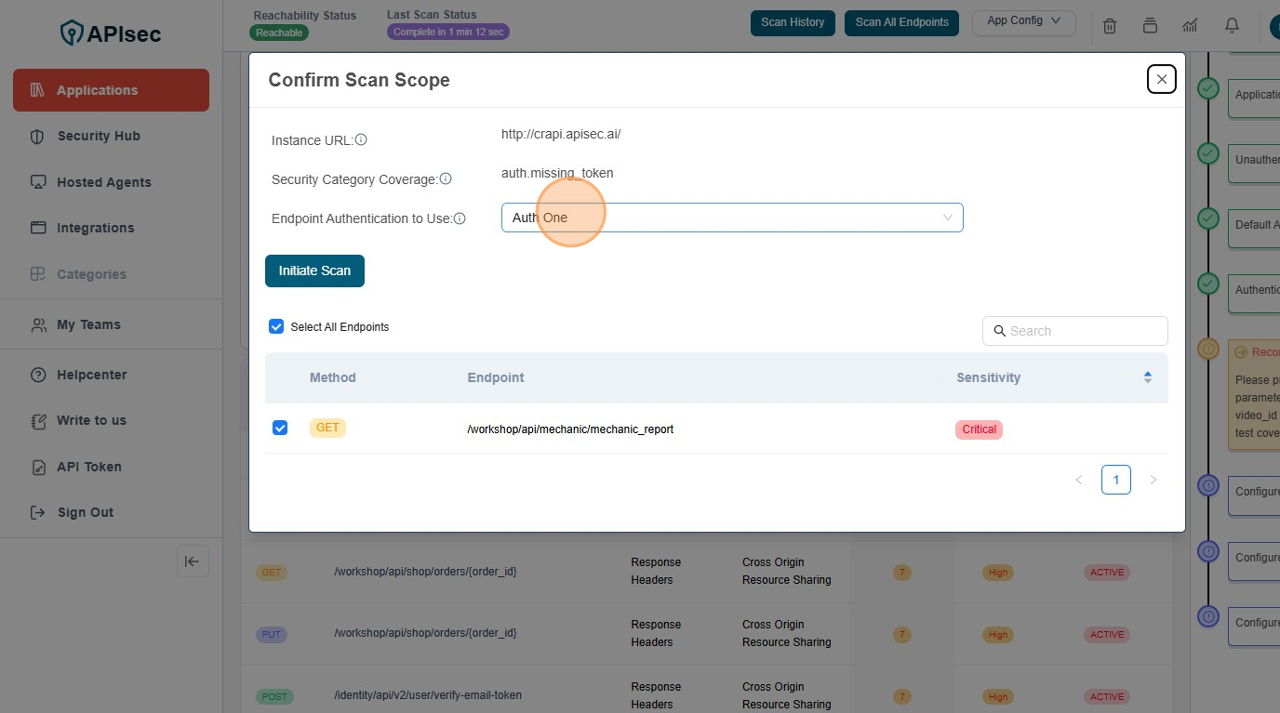
- Click on Initiate Scan