Overview: Authenticated API Scanning
What is Authenticated API Scanning?
Authenticated API scanning is the process of testing API endpoints with valid authentication credentials such as API keys, OAuth tokens, or session-based authentication. This approach allows security teams to evaluate how an API enforces authentication and authorization controls, ensuring that sensitive endpoints are not accessible to unauthorized users and that role-based access restrictions function correctly.
Unlike unauthenticated scans, which assess what an external attacker can access without credentials, authenticated scans provide deeper visibility into the security posture of protected API endpoints. This helps uncover issues such as broken authentication, improper authorization, and privilege escalation risks.
Why Perform an Authenticated Scan?
- Validates Authentication Mechanisms
- Ensures that APIs correctly enforce authentication before granting access.
- Identifies weaknesses in authentication flows, such as improper token validation or session handling issues.
- Tests Role-Based Access Controls (RBAC)
- Confirms that users only have access to endpoints based on their assigned roles.
- Identifies privilege escalation risks where lower-privileged users may access restricted resources.
- Detects Broken Object-Level Authorization (BOLA)
- Evaluates whether authenticated users can access or modify data that belongs to other users.
- Helps prevent unauthorized data access issues, a common vulnerability in APIs.
- Simulates Real-World API Interactions
- Authenticated scans allow testing of business-critical endpoints that require authentication.
- Helps assess security across different API usage scenarios, including multi-step authentication flows.
- Complements Unauthenticated Scanning
- Provides a full security assessment by analyzing both publicly accessible and restricted API endpoints.
- Ensures that authentication mechanisms protect sensitive data effectively.
When to Perform an Authenticated Scan?
Authenticated API scanning should be performed:
- Before an API goes live to verify authentication and authorization security.
- As part of routine security testing to identify new vulnerabilities introduced during updates.
- After changes to authentication or authorization mechanisms to ensure continued security.
- During compliance audits to validate adherence to security best practices (e.g., OWASP API Security Top 10).
How Authenticated Scanning Fits into API Security Strategy
Authenticated scans are essential for:
- Ensuring secure authentication and session management.
- Validating authorization controls to prevent unauthorized access.
- Detecting API-level security issues that may not be visible in unauthenticated scans.
By integrating authenticated scanning into security workflows, teams can proactively identify vulnerabilities and ensure that authentication and authorization mechanisms work as intended.
Navigate to URL
Open your browser and visit: https://<your-tenant>.apisecapps.com
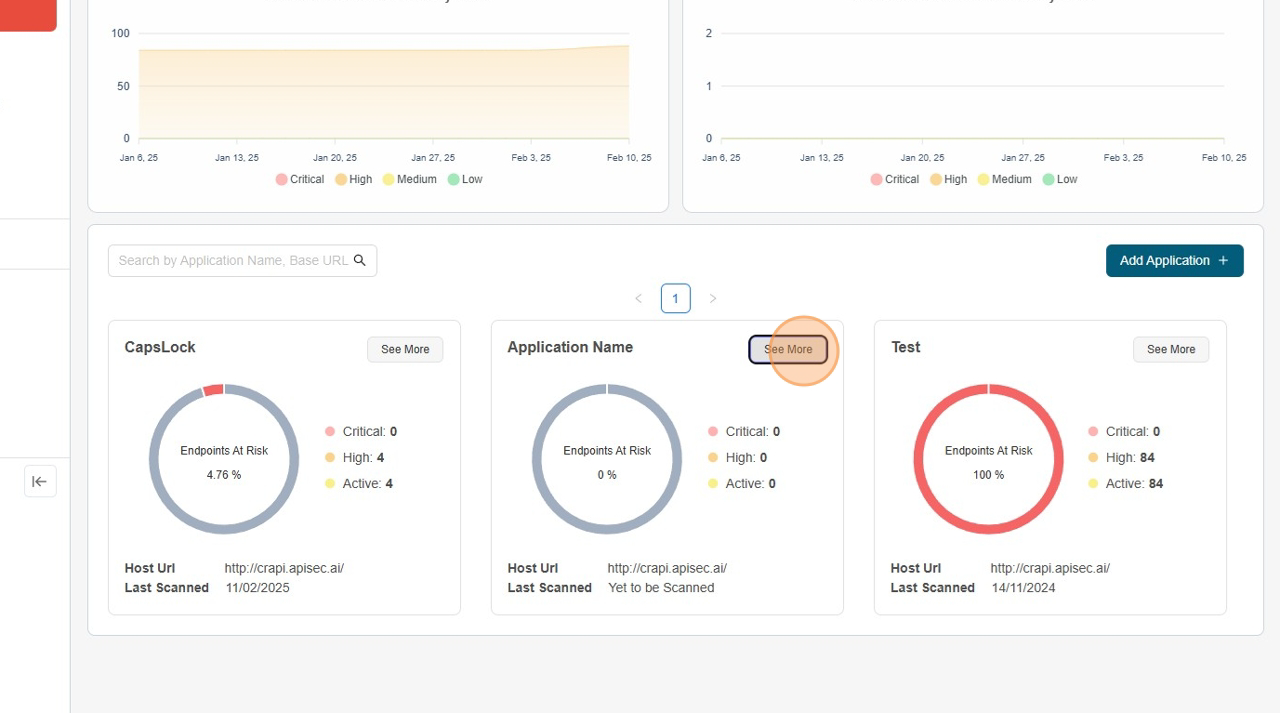
Visit the application
- Click on "See more" to open the application
How to perform a Authenticated Scan
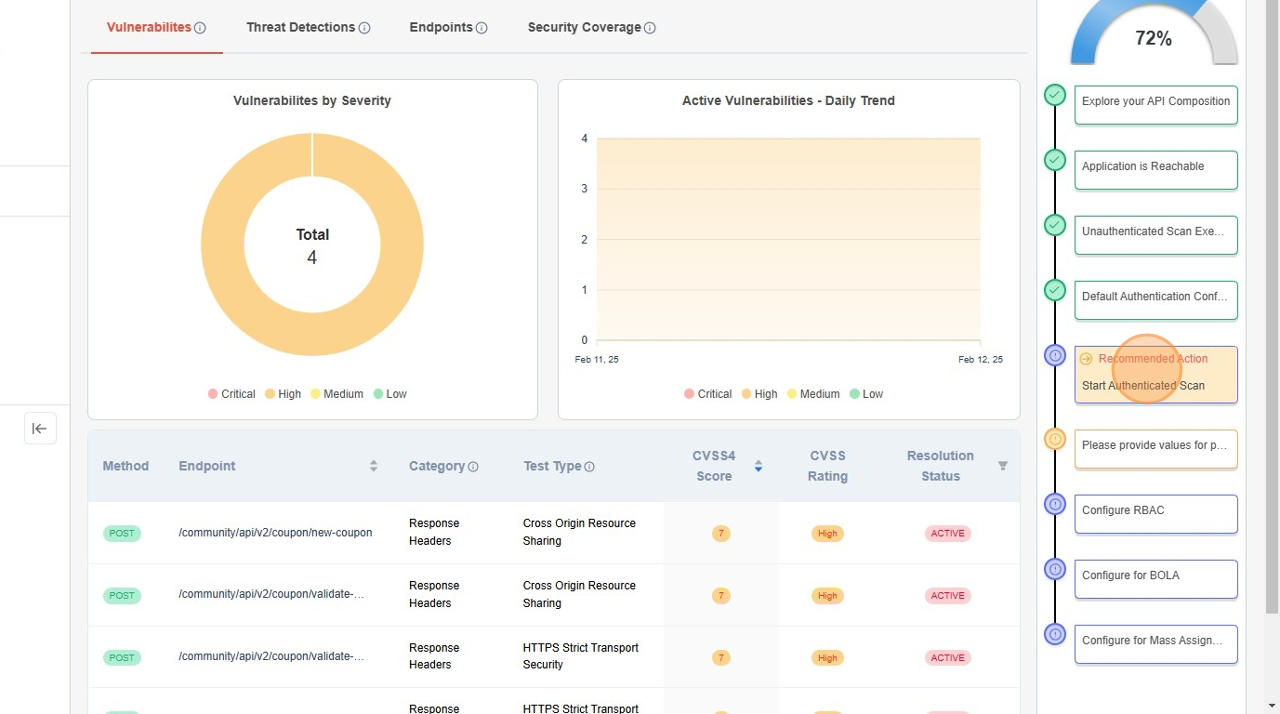
There are two ways to start with setting up the authentication.
- From App Model
- From Application Details page
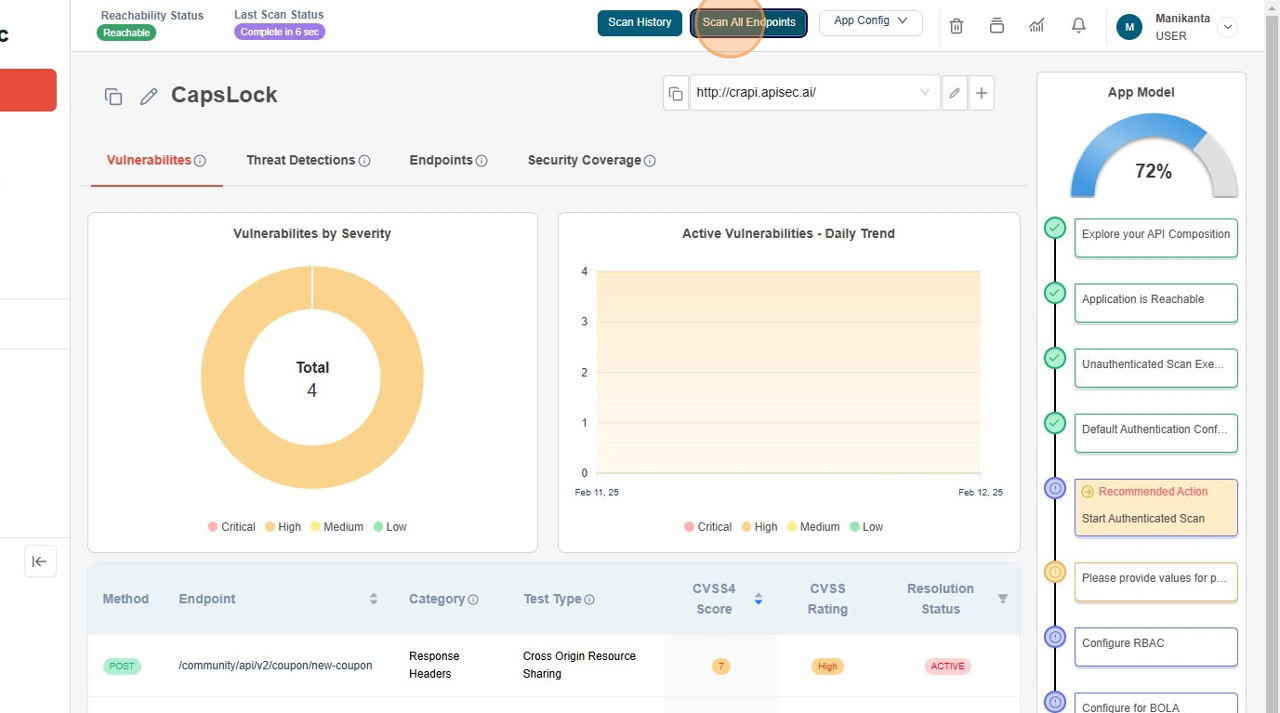
Perform an authenticated scan
Here first we select those API on those we wanted to scan.
- Click "Scan All Endpoints"
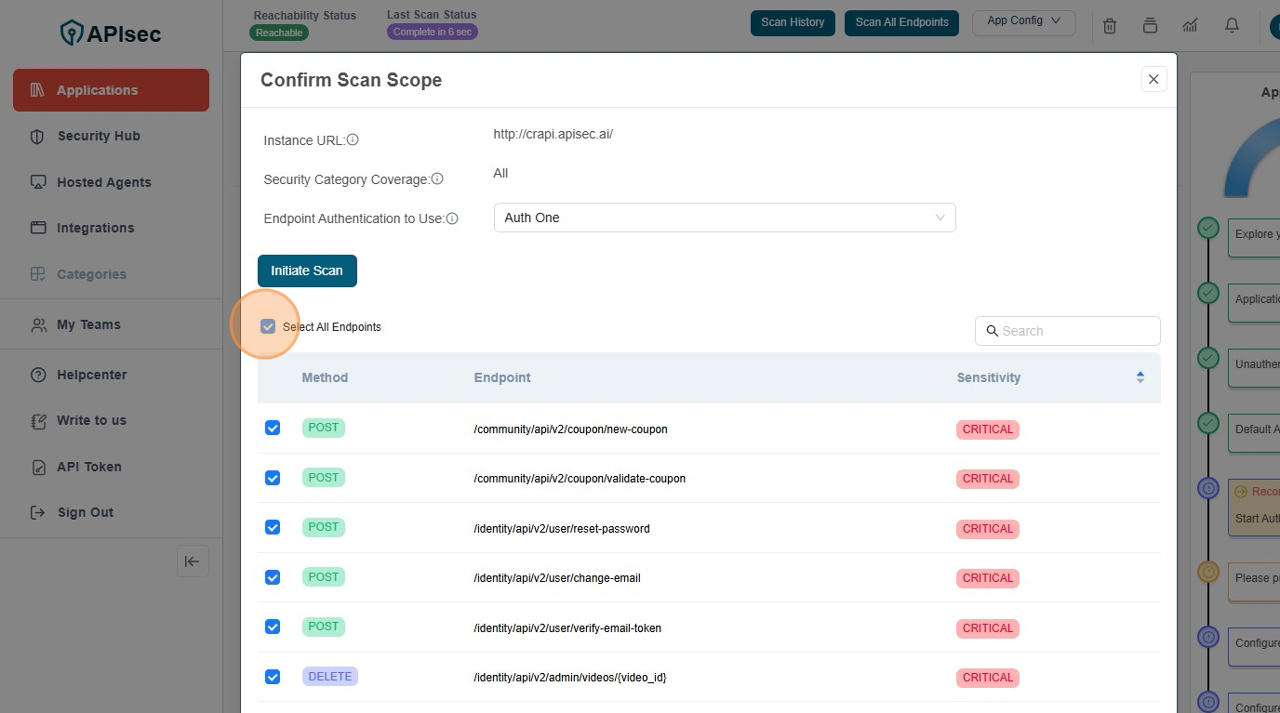
Confirm the Scan Scope
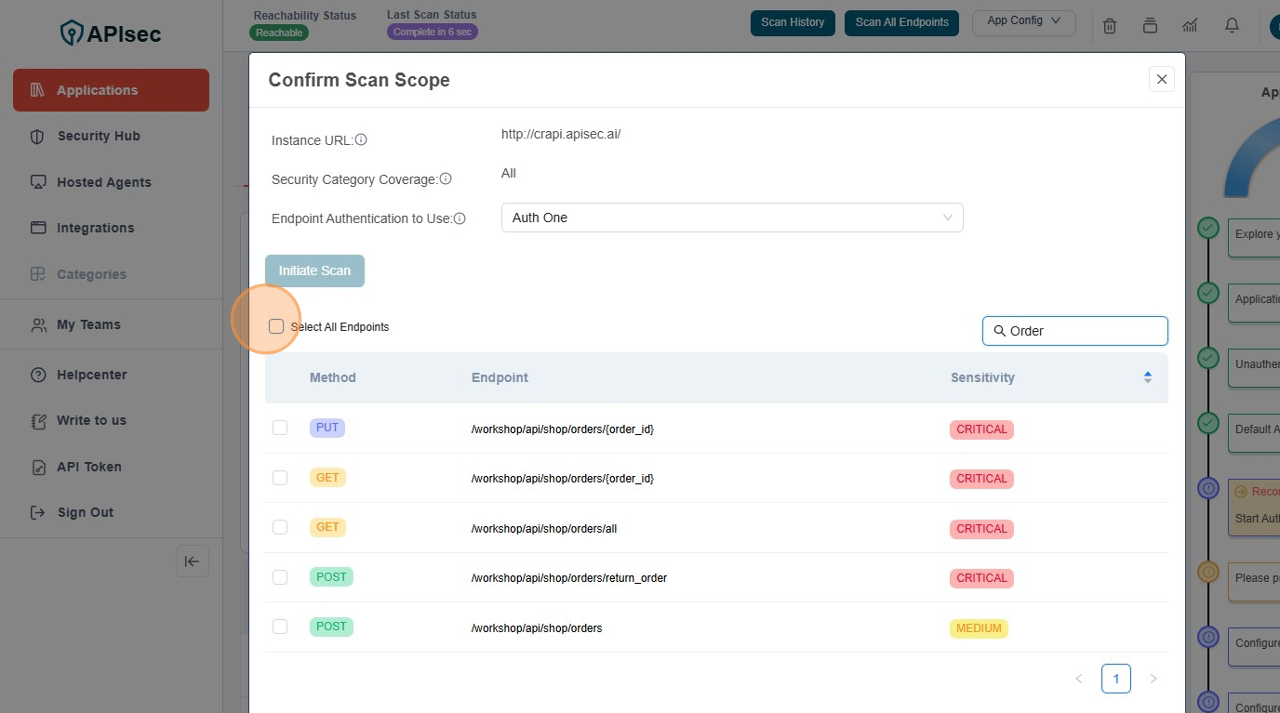
Here you can customize your scan, like search "Orders" api and then initiate the scan.
Make Sure the under the head Endpoint Authentication to Use should show you the Authentication list in dropdown which you create using Configure an API Authentication
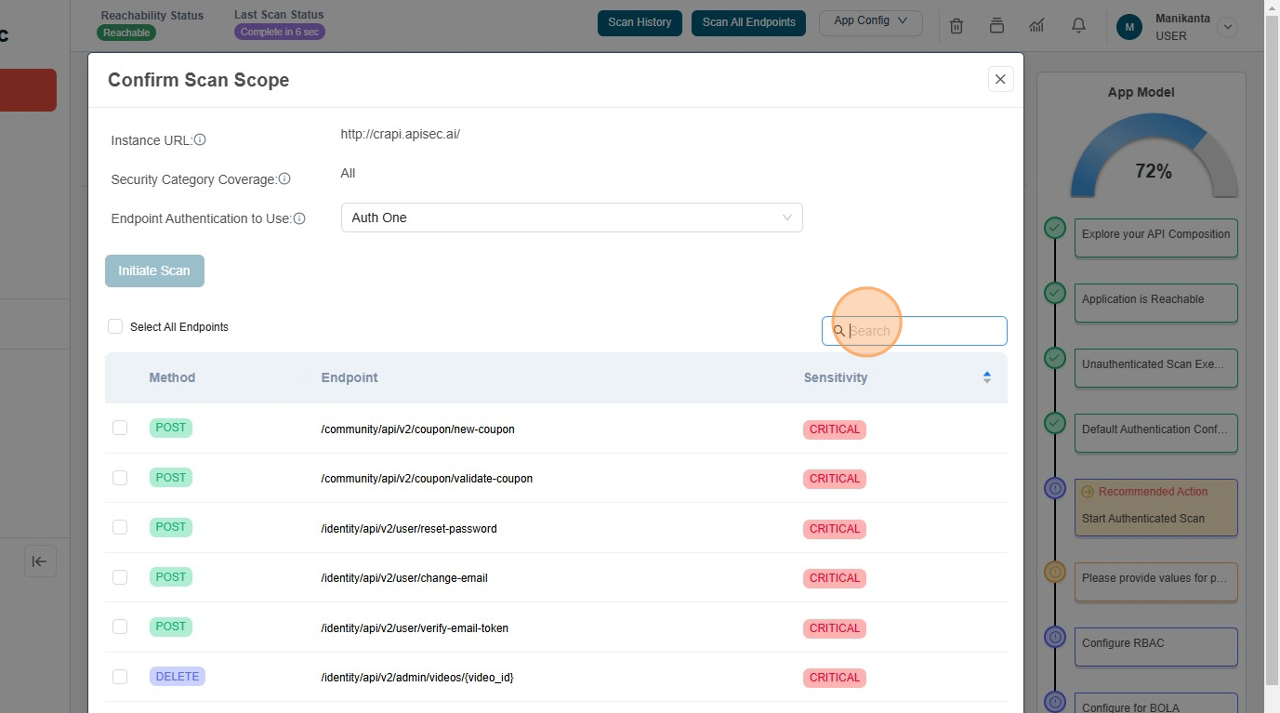
- Unselect all endpoints, Click the "Select All Endpoints" field to remove all selection of API's

- Type "Orders" in Search field.
- Click the "Select All Endpoints" field; to select the all Orders related API's
- Check the Authentication Dropdown under the head of Endpoint Authentication to use
- Click on Initiate Scan
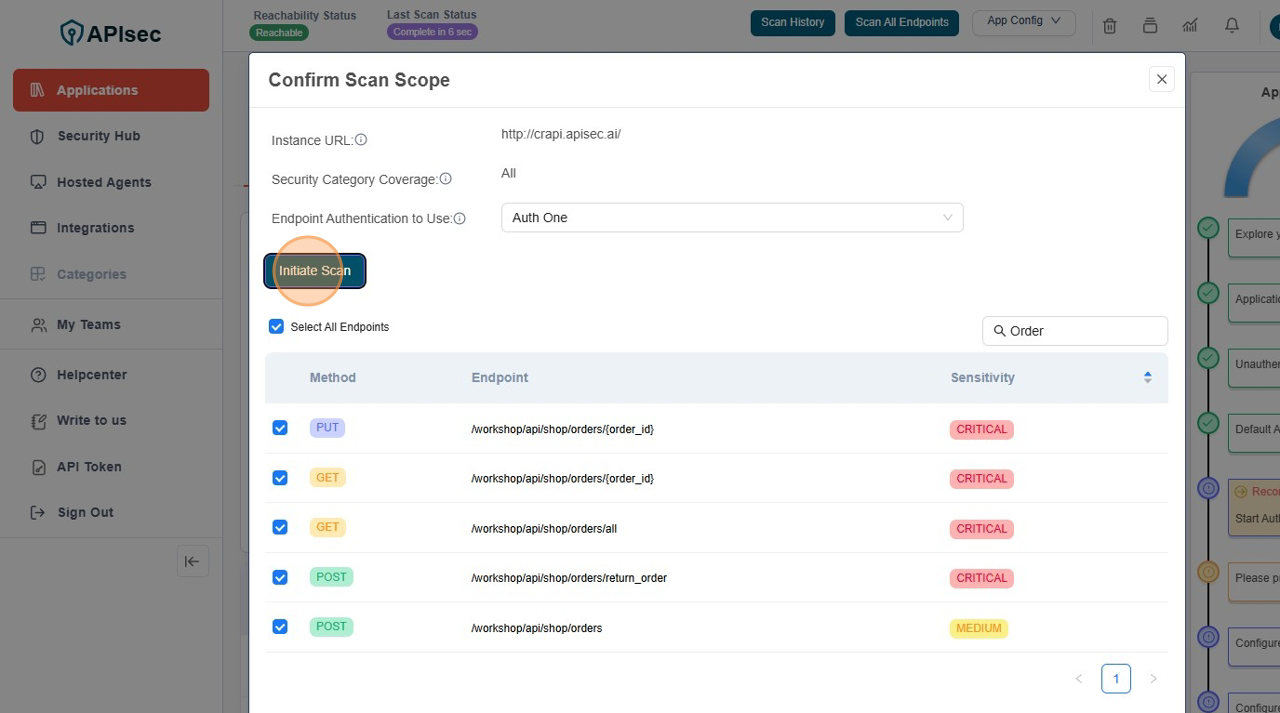
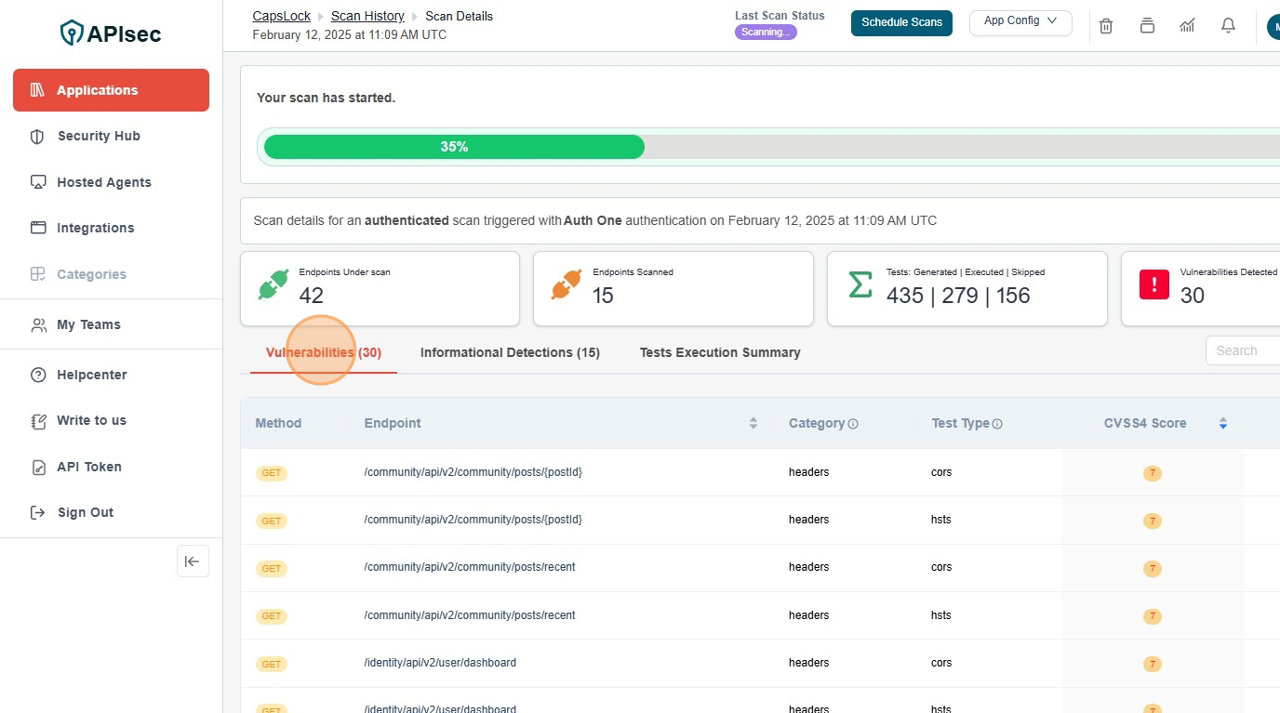
Confirm the Scan has started
- You can scan progress bar in top of the Application Name
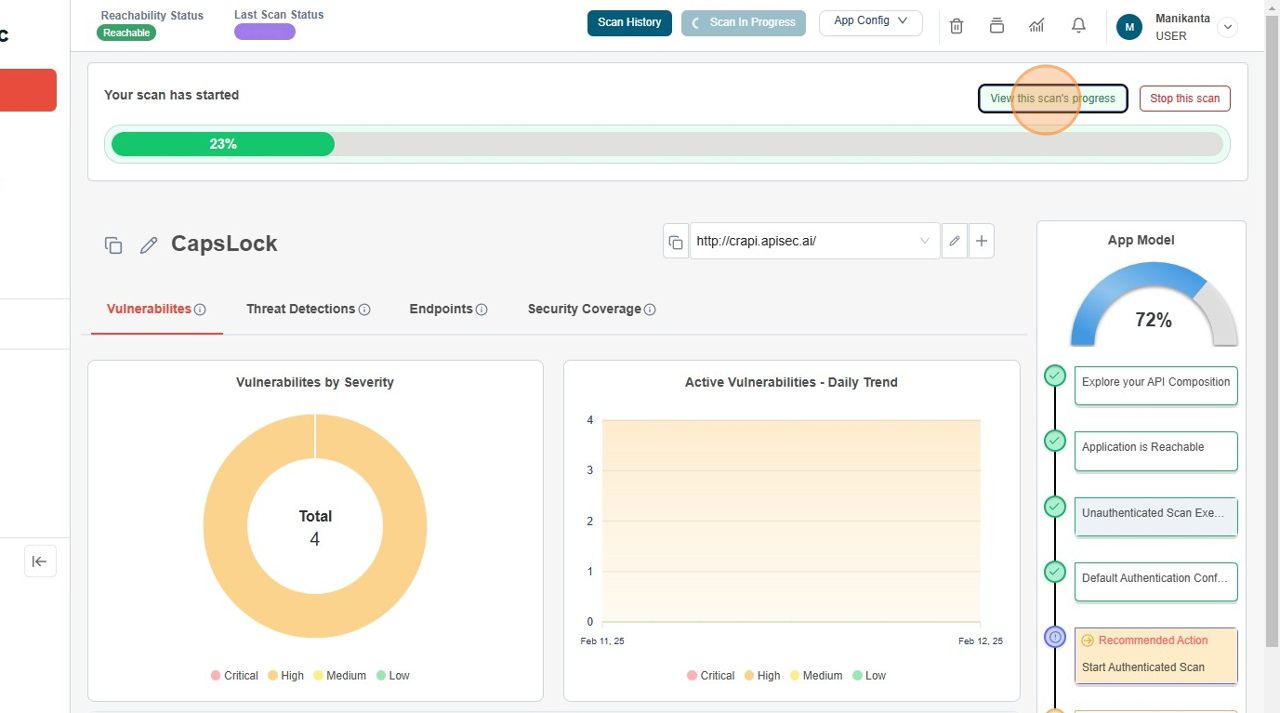
Scan Details Page with current scan's progress
Click "View this scan's progress"